Best WIFI cards /Wlan KisMAC Compatible
Also know as: KisMAC Network Adapters, USB Injector, USB NIC (Network Interface Card) or Kismac USB Re-Injection Adapters
Not all USB Network Adapters are created equal. If you have read some of the comments left, you have realized that buying the right "USB Thingy" will make your life a breeze Vs. a freakin' nightmare.
Some Networks Adapters will work, some may work in the future, and some will never work.
For the "Never" and "In a Distant Future" I will not spend too much time: For the sake of you, don't try to finagle or to save $5, you'll end up in a nightmare: Been there, Done that.
For the Adapters that work right away, we have 3 types: The Bad, the Ok , and The Excellent.
If you believe that an higher price will determine The Excellent, you're in for a big surprise!
So, enough suspense, here it is:
Best WiFi Card compatible with KisMAC
International buyers: See Below
Alfa AWUS036H + 5dBi + Mount + FREE SHIPPING Compatible Mac / Windows / Linux / Ubuntu Card + USB + Antenna 5dBi + CD + Mount
Alfa AWUS036H V5 1000mW Compatible Mac / Windows / Linux / Ubuntu
Card + USB + Antenna 5dBi + CD is about $29
The Best Deal is: Same as above + 9 dBi Antenna (One 5dBi + One 9dBi) + Suction Mount Cup Alfa AWUS036H V5 1000mW + 5 dBi + 9 dBi + Suction Cup Mount + USB + CD
Price about $35 for the bundle. Mount alone is ~$4, 9dBI antenna alone ~$9
CANADA: Amazon.ca
GERMANY Amazon.de
UK Amazon.uk Without Mount Dock With Mount Dock
This Ref only. The Alfa AWUS036NH (2000mW) is not KisMAC compatible. All Drivers for the AWUS036H , KisMAC compatible are located here. Windows, Mac, Linux included.
Here is an example on how good is that card:
( Click on Read More )
The highest form of ignorance is when you reject something you don't know anything about.
Wayne Dyer (b 1940)
Kismac: The Ultimate WiFi Stumbler

How to Crack WEP / WPA Step by Step
KisMAC for Dummies & Step by Step KisMAC Tutorial
KisMAC Tutorials for dummies, beginners & advanced users
Update of update : a Brand New Improved Video in HD, con la musica muy entertaining is available at the end of this post. it should cover KisMAC 101 and walk you trough WEP and WPA cracking
For the curious, advanced users and KisMAC geniuses , we have the following articles available:
Best Wifi Card for KisMac about 20 X more powerful than Airport or Hawking
Troubleshooting KisMAC
KisMAC Q&A
Cracking WPA with KisMAC
KisMAC Resources
KisMAC Deep Digging , Advanced Features
How To Install Aircrack On Mac
Before you post a question, PLEASE be sure to Read the 3 following post:
KisMAC + KisMAC troubleshooting + KisMAC Q & A
Once you are sure that the answer to your question can not be found, Please, Post your question in the Q&A Article: CLICK HERE.
ALL QUESTIONS WITHOUT KisMAC Version and OS Full Version will be ignored. Please Include Model and FCC number of the Network Adapter (the USB thingy) if applicable. And YES the FCC number is on it! and NO, it's not the MAC address.
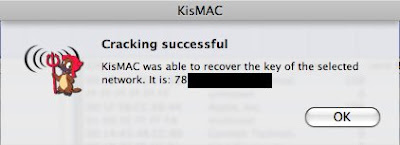
Cracking WEP with Injection
Cracking WEP without Injection (Airport, Airport Extreme)
Cracking WPA
KisMAC Troubleshooting Guide
KisMAC Resources Dictionary file, Password list, etc
KisMAC is a free WIFI Network discovery tool and has a large array of powerful features: Detection, Authentication, Injection, GPS, and the ability to crack WPA & WEP keys.
KisMac is really powerful and leave Windows based NetStumbler in the dust. By a large margin.
Kismac is not for absolute beginners and the first step with KisMAC is to read the FAQ. The second step is to read the FAQ again.
Just a little legal warning:
- It is illegal to download, possess, and/or use Kismac in Germany, Austria, Switzerland and Lichtenstein (StGB § 202c)*
- It is illegal, in most countries, including the USA, to crack or attempt to crack, penetrate, listen to, intercept, or “Inject” any WI-FI network others than yours, or Networks where the unequivocal permission was not given to you by the rightful owner.
- Kismac is a tool that should be used on the sole purpose to check and/or verify, audit your own network
Now that I warned you :-) you can enjoy it!
Cracking WEP with Re-Injection
Whatever you do, if you have an injection device (WIFI card or USB Adapter) DO NOT install the drivers of the card / USB adapter.
DO NOT INSTALL DRIVERS FROM THE CD PROVIDED WITH THE DEVICE unless you have read this post
How to Crack WEP Step by Step
This tutorial is solely for you to audit your own network. I take no responsibility whatsoever, implied or not.
If you NEED an access, just ask politely your neighbor and either share the cost or discuss with him. A six-pack can be used as lubricant.
Cracking with Injection device

(Hawking HWUG1 shown here, RT73 Chipset. DO NOT BUY THAT ONE
Read review and comparison before: best card is here
Best Wifi Card for KisMac about 20 X more powerful than Airport or Hawking
The most successful method by far, with one little issue: you will NEED a Re-injection device: Either a USB WIFI Adapter or a WIFI card.
But, here comes the trick:
-You cannot use any WIFI card: You must use specific ones.
The list of “approved” hardware is here: http://trac.kismac-ng.org/wiki/HardwareList
As of today, you can NOT inject packet with your Airport / Airport Extreme Apple card alone.
Step 1
Download KisMAC from a trusted source such as: http://trac.kismac-ng.org/wiki/Downloads
Install KisMAC
Plug your Injection device, Whatever you do, DO NOT install the drivers of the card / USB adapter, or you may dearly regret it.
Start KisMAC
Step 2
On the Tab KisMAC >>> Preferences >>>Drivers
Select your Injection device i.e. : “USB RT73 device”
If you have a doubt on what to choose, check the "approved" hardware list.
Click on “Add”
Check box “Use as primary device”
Select
In some Cases, Ch 12-14 can pick up interferences from other home devices: Stay within 1-11 !
Check box “keep everything”
Close Dialog Box
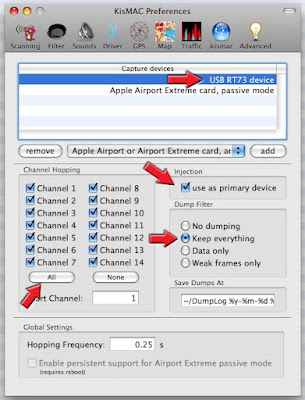
Step 3
On the main screen, select “Start Scan”
KisMAC is now listening to the accessible networks
Look for a network with a WEP key (column “ENC”), a good signal as well as traffic (see Packets and Data)
OR
Enter “WEP” on the search box (top right) and select “encryption” to filter the results
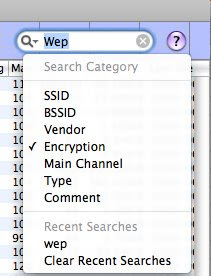
If the Column ENC is “NO”, the network is OPEN: No need of cracking anything
Once you have selected a network, look for the CHANNEL of the network, i.e 1, 2 etc …
Go back to Preferences >>>> Drivers
Select only the Network selected i.e 1
Step 4
Let KisMac work for 5 minutes collecting data
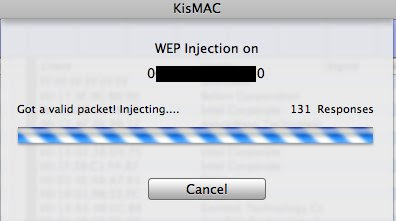
On the “NETWORK” Tab, select “Reinject Packets”
KisMAC will now try to reinject packets to speed up the process
Keep an eye on the “Unique IV’s” number, once it has reach at least 130,000 (200,000 is recommended) you may start considering cracking.
Step 5
Once you have collected enough, On the NETWORK Tab, Select “Crack” >>> “Weak Scheduling Attack” >>> “Against Both”
KisMAC will now try to crack the key…
Reminder: the more Unique IV’s you have collected, the greater are the chances to crack the key.
I have experienced crack as fast as 10 sec with 200,000 Unique IV’s (on a 64 bit key) and sometimes 30 minutes with only 110,000
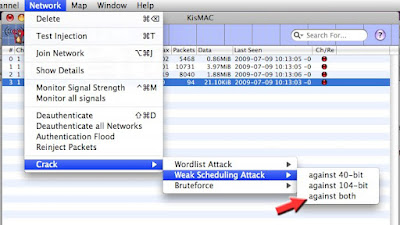
If you know for sure that the key is either 40 bit or 104 bit, then select the appropriate one. If you are not sure, select "both"
40 bit is a 64 bit (40+24)
104 bit is a 128 bit (104+24)
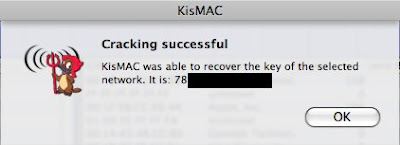
If you have followed the steps, you should see something like that appears :-)))
remove the semicolon, and there you have it, or take a look at the main screen under Key or ASCII Key
How to crack WEP / WPA with Airport Extreme, Passive mode
WITHOUT Injection Device (Airport, Airport Extreme Alone)
WEP attack
Step 1
Read the FAQ http://trac.kismac-ng.org/wiki/FAQ
Step 2
Read the “Newbie Guide” http://trac.kismac-ng.org/wiki/NewbieGuide
Step 3
Download KisMAC from a trusted source such as: http://trac.kismac-ng.org/wiki/Downloads
Last build is 0.3.3
Install KisMAC
Start KisMAC
Step 4 (without an Injection Device)
On the Tab KisMac >>> Preferences >>>Drivers
Select your card. (Capture devices) i.e : Airport Extreme Card, Passive Mode
Click on “Add”
Select Channels 1-11
Close Dialog Box, and select “Start Scan” on the main window
A dialog box opens and load the card. Your Admin password may be required.
Step 5
KisMAC is now listening to the networks accessible
Look for a network with a WEP key (column “ENC”), a good signal as well as traffic (see Packets and Data)
If the Column ENC is “NO”, the network is OPEN: No need of cracking anything
Once you have selected a network, look for the CHANNEL of the network, i.e 1, 2 etc …
Go back to Preferences >>>> Drivers
Select only one Network selected i.e Channel 1
Step 6
Be patient: open a beer, pour yourself a nice glass of wine or have a nice cup of coffee.
Without an injection device, you will need to collect a minimum of 130,000 unique IV’s before you can start cracking a 40/64-bit WEP
Recommended:
200,000 Unique IV’s for weak scheduling attack on a 40/64-bit WEP
1,000,000 Unique IV’s for weak scheduling attack on a 104/128-bit WEP
It may take a long time (based on: Network traffic, re-injection or not)
Those are recommendations. Weak Scheduling is basically a statistical attack: The greater the number of IV's collected , the greater the chances.
Are you in a hurry? : Capture with KisMAC, Crack with Aircrack-ng
You can have a successful recovery with as low as 21,000 IV's
Step 7
Once the packets are collected, Go to the tab “Network” >>> Crack and select the method,
For a start, I would suggest: “Crack” >>>”Weak Scheduling Attack” >>> “Against Both”
Once started, you’ll have to wait between 5 and 20 minutes depending on your machine for KisMAC to try all the keys.
The more packets you have collected, the better are your chances to be able to crack the key: The WEP Attack is Statistical, hence ....
WPA crack / Attack
>>>>> Packets RE-Injection DOES NOT WORK on WPA attack <<<<<<
>>> I said RE-Injection and not "Injection"
In order to crack a WPA key, you'll need the handshakes, a serious dictionary file or fileS and a LOT of CPU time. Hours and probably days of it. (read the "I am bored part" at the end)
You first need to capture 4-way EAPOL handshakes (connection between the computer and the network) -When captured, you'll see the Ch/Re red dot turns green. You are ready to try...
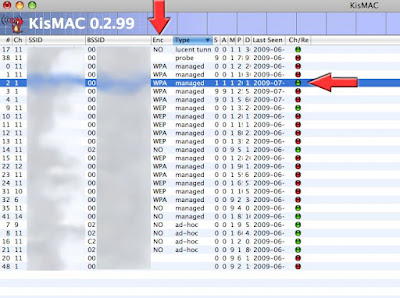
To speed up the process of capturing the 4-way EAPOL handshakes, you can try a deauthenticate attack: it will force the network to shutdown and restart, hence speeding up the process.
Go to Network >>> Deauthenticate
Some network may recognize the attack and change channel.
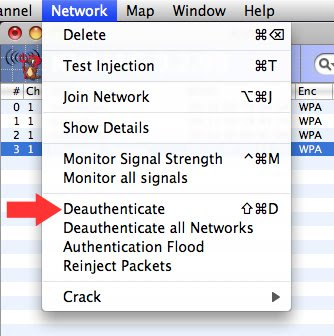
Once the Ch/Re is ready, Go to the tab "Network" >>Crack >>WPA
It will then ask you for the dictionary file, select the file you want to use, and start...
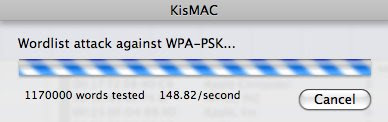
Nota Bene:
KisMAC will try every word (from the list provided) to attempt to crack the key, hence it may take a lot of time....if you have a slow machine, be really patient.
I have a not so bad machine, and I run about 170 words per second. You can leave a comment with your config and speed for me to compare.
Mine: MacBook Pro 2.5GHz Intel Core 2 Duo + 4GB DDR2 SDRAM : about 170 Word/sec
As for the Dictionary files, you can find links on the KisMAC website or take a look at the "RESSOURCES" post.
Note on dictionary files:
Wordlist = dictionary file
- The words are tested "as is" and not in combination.
Example: the password is "I love Kismac"
If your dictionary contains the words "I" + "love" + "Kismac" it will NOT work, your wordlist must contain the exact (verbatim) "I love Kismac" as a word to successfully attempt to crack.
The files must be a text format .txt and contain a empty line at the end.
KisMAC Troubleshooting Guide , KisMAC Issues, KisMAC Ressources are on the NEXT post....
KisMAC for Windows, ditto...next post
WPA: Wordlist links and files Download are here
Labels:
Crack WEP,
Crack WPA,
KIsMAC,
Network Audit,
WIFI Crack,
WIFI Stumbler
KisMAC Ultimate Stumbler Ressources & Troubleshoot
Troubleshooting KisMAC
KisMAC Tutorial
Resources
Troubleshooting KisMAC
KisMAC 0.3+ Bugs
KisMAC 0.3+ Issues
KisMAC 0.3+ Not Working
KisMAC 0.3+ Bugs, KisMAC 0.3+ Issues, KisMAC 0.3 Not Working
-Did you noticed that KisMAC 0.3 is for Snow Leopard 10.6 ? and not for 10.5? ok....
Can't Scan with KisMAC 0.3
"NOTE: If a previous installation of KisMAC has been used, please make sure to delete the following files, if they exist:" ( '~' is your home folder) (Using App Cleaner IS a GOOD IDEA)
Message
Could not instantiate driver. KisMAC has not been able to load the driver backend
Could not initiate driver. KisMAC has not been able to……
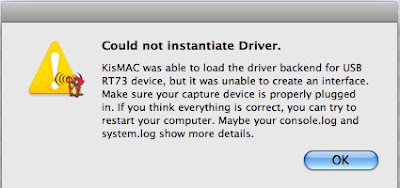
Whatever you do, if you have an injection device (WIFI card or USB Adapter)
Possible causes:
You have NOT selected "Use As Primary device"
You Have NO Drivers selected
You have Selected the wrong one
Your Chipset is not supported (see Hardware list)
The Chipset of your USB Network Adapter is not correct (See FCC Number)
In order to avoid those issues => Best Wifi Card for KisMAC
If you look in your console.log (Spotlight >> Console)
you'll probably see a lot of lines with KiMAC as "sender" and an error messages such as:
Solutions
Select Appropriate Driver or use the proper USB Network Adapter. You may need to Force Quit the application
You have installed drivers provided with the CD of your USB Network Adapter.
Solution 1:Time machine? if you have Time Machine set up, pat yourself on the shoulder: smart guy!
If not, time to think about it and move onto Solution 1.5
Solution 1.5:
Uninstall the drivers* and the all shebang provided with your injection device
including the proper .plist for Kismac
use AppCleaner to remove all .plist
OR if you had a previous install, remove the following, if any:
~/Library/Preferences/de.binaervarianz.kismac.plist (where '~' is your home folder)
~/Library/Preferences/com.kismac-ng.kismac.plist (where '~' is your home folder)
~/Library/Preferences/org.kismac-ng.kismac.plist (where '~' is your home folder)
(told ya' use AppCleaner)
Solution 2: If, after uninstalling the drivers*, the problem persist, -and- you have trouble with your Airport Extreme, you may be in for a shitload.
Uninstall KisMAC, and re-install
Injection does not work
- Check that your device (USB/Card) is able to inject, => see Best Wifi Card for KisMAC
- Test injection: Tab “NETWORK” >>>”Test injection”
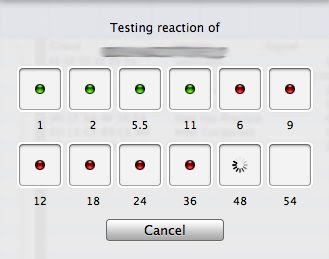
- Check that you have checked the box “use as primary device” in tab Preference >>> Drivers
- Check that you have the proper driver/chipset selected i.e. USB RT73 or USB RT2570 (Preferences >>>Driver)
- Check that proper channel is selected. One channel only: You cannot inject while Channel hoping is selected
- As stated, be very careful to have the proper chipset, otherwise: nada!
Word of advice, I would suggest you to test the hardware in a “brick and mortar” shop before you buy something that will not work, or take my word and experience for it, and purchase the best card available for KisMAC, it's less than $35 and allows you to get a signal up to 1 mile. it's 20x more powerful than an Hawking.
Reinjection Not Working
If you have tested the Re-injection and your card should re-inject packets, you may have the following issue(s)
- Your card is not powerful enough for the signal to reach the AP => get this one: Best Wifi Card for KisMAC
- There is not enough "good" traffic on the network. IV's (Initialization Vectors) are only about 5% of good traffic.
You also have the remote possibility to have encountered a very rare breed of APs: The one equipped with "WIPS" (Wireless Intrusion Protection System). In that case, Passive Mode is the solution.
If you want to know more, here is an excerpt from the KisMAC FAQ.
Packet reinjection is a very advanced WEP cracking technique. Be aware that this is the bleeding edge of technology, so it might not work every time. When you use this attack, KisMAC will try to find packets that will cause another computer to respond. The program will then send these packets over and over again. If KisMAC detects answers, it will go into injection mode..... Please be aware that all detections are of a heuristic nature, therefore it might not always be working"
Source: KisMAC
Packet collection is very slow
It’s probably because the network is not very active (low traffic). Just go on YouTube, watch few videos and the packet collection should increase very quickly.
Crack does not work
-Well, as stated in the FAQ, Injection is the bleeding edge of this technology, and I have experienced myself some failures with my own network: I was unable to crack my own key with more than 1,000,000 unique IV’s.
Other possible causes:
The key was changed during the collection
You have selected a 40/64-bit WEP when the key is 104/128-bit WEP, so in doubt, play safe and select both
You have encountered a SOL error: Shit Out of Luck
The wpa key could not be recovered because of the following reason:
the key was none of the tested passwords.."
Most likely, your dictionary file does not contain the exact password, read the article about wordlists.
WPA Reinjection Does Not Work
please note that RE-Injection and Injection are not the same.
-WPA RE-injection will not work, you can only RE-inject on WEP network, if you have an injection device. (i.e When you Deauthenticate , you are injecting frames)
KisMAC Crash on WPA Wordlist
KisMAC Can't Perform Injection Test
This is bug with KisMAC 0.3.3 while on 64-bit
Go to Applications >> KisMAC.app >> Get Info
Check "Open in 32-bit Mode" and restart.

Could not load Airport Driver
KisMAC could not attach to the Apple Airport Driver
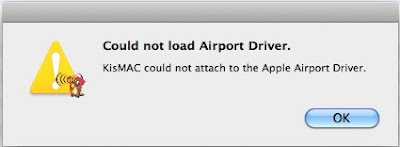
KisMAC could not attach to the Apple Airport Driver
In Preferences >>> Driver
You may not have selected any Driver (Apple Extreme, RT73, etc etc )and pressed the "Start Scan" button multiple times, this provokes a freeze and return this error.
The "Start Scan" button looks like the one in the picture below (button engaged)
The solution is a Force Quit and to select a correct driver in Preferences >> Driver
KisMAC could not attach to the Apple Airport Driver
Cause: Airport, Airport Extreme in ACTIVE Mode
This issue is fairly new and is related to the brand new Snow Leopard (10.6)
You have this error because you have selected Active Mode
Close KisMAC , re-open and select Passive Mode.
Do not use Active Mode with OS X 10.6 until further notice.
No Driver Selected
Please Select a WIFI Driver
Go back to Preferences and Select a Driver
i.e. Airport Extreme Passive Mode, USB RT73 Device, or else.
KisMAC Ch/Re Gem
The Ch/Re Gem is situated on the last column, right after "last seen"
Ch/Re stands for Challenge / Response
The Gems have 3 colors possible: Green, Orange and Red and the meaning will depends on the type of encryption of the Channel/Network
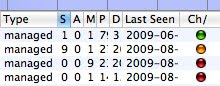
Enc = NO
The Network has no encryption (Open), (under column "Type") the Ch/Re Gem is green by default
Enc = WEP
The Network is encrypted by a WEP key, the Ch/Re Gem is red by default and indicates that Kismac does not have recovered a key (yet) No Challenge or No Reponse
Green Challenge or Response
Orange has a Challenge OR a Response
Enc = WPA
Red: No handshakes captured, don't even try a wordlist
Orange: Capture Started (?)
Green: Handshake Captured
KisMAC Freezes
KisMAC Hangs
KisMAC Freeze, KisMAC is hanging, KisMAC Freezes, PinWheel KisMAC
If KisMAC Freezes after few seconds, and hangs (Pinwheel) the first cause that comes to my mind is that you are using (listening to) the wrong channels.
If you are in USA, you should not be using Channels 12,13 & 14 (Europe and Japan)
If you are in Europe, You should not be using Channel 14 (Japan Only)
Just uncheck 12,13 & 14, that should resolve the problem.
Possible cause: Channels 12,13 & 14 are close to the microwave range and cordless phones (old ones)
It's possible that you are listening to your coffee or pop corn.
A second cause could be a large number of router using the same channels (often Ch 6), it may also create issues on your own network. In that case, just switch channels and you'll see an improvement in your Network quality
Can't Collect IV's
Can't Collect Packets
Packets Collection is very slow
I have received a lot of questions about this issue. The most probable cause is a non active network.
A non active or slow network (low traffic) is what makes the collection very slow.
KisMAC in passive mode is like trying to collect rain water: The more it rains, the more you can collect. That simple! If it does not rain .... or very little ... you got the idea!
A good wifi card will help you solve this issue
After receiving 10 + questions on the subject, here is an example of a near silent network:
As you can see 614,847 management packet (beacon) and only 25,945 Data Packets (the good stuff)
so, 615,902 junk.
This network is simply "on" but not used, hence, as long as there is no valid traffic, you need to be more than extremely patient
Other possible cause: You may be listening to a Probe, or a Router not connected to the internet, or someone that left his router on, but does not use it. Read the post till the end...
Here is what I have tested with active networks, and very active networks. It clearly shows that the collection of IV's is related to the traffic.
The test is with an Airport Extreme, Passive Mode, NO Re-injection
It took me 5 minutes to reach 130,000 IV on very active network, and 126 min on Active.
For the numerous persons that still believe that Kismac can not crack on Airport Extreme, the following is going to be surprising:
Very Active Network
Time : 0:02:05 2min, 5 sec
Bytes: 83.42 MiB
Packets 58,423
Unique IV in 0:02:05 = 57,016
U IV/Sec = 456.12
Theoretical Time to reach:
130,000 = 285 sec = 4.75 min
200,000 = 438 sec = 7.30 min
300,000 = 658 sec = 11.0 min
Active Network
Time 03:23:50 3hrs 23 min 50 sec
Unique IV's in 03:23:50 = 210,216
U IV/Sec = 17.18
Theoretical Time to reach:
130,000 = 126 min
200,000 = 191 min
300,000 = 285min
1 As Kismac has loaded the Airport Driver, he has control over it. Proof that this is on Airport and not on USB
2 Time
3 Packets
4 Unique IV's Collected with Airport Extreme on Passive Mode.
a Kismac still on Airport
b Time 2min and 5 sec
c Unique IV's Collected with Airport Extreme on Passive Mode. = 57,016 in 2 minutes, roughly 11 min to 300,000
d Bytes = 83.42 MiB for 57,000 IV's
Hence, Kismac does work on Passive Mode, and yes, you can crack on Passive mode without Re-Injection. If you can't, it's probably because of the network quality or simply because you may have selected a wrong parameter.
Test Your Own
One way to be sure is to test your collection speed:
Go to a friend's house , Start KisMAC , and ask your friend to watch multiple Youtube Video on its network. You want to push the router to the max.
You'll be then able to see if the issue is due to slow network or not.
While you're at it, ask your friend to run KisMAC too: You'll be surprised to realize that you can:
A) exchange PCAP dump files and try multiple cracks on multiple networks
B) if using Re-injection, notice that ONE device will make ALL Macbooks able to pick up the responses
Macbook does not detect edimax ew-7318usg
It's NORMAL! Don't panic!!!
Your Macbook can NOT detect your Edimax, because your driver(s) are not installed.
KisMAC will detect your edimax, under Preferences >> Driver >> use USB RT73 Device
DO NOT INSTALL the Drivers provided with the install CD of your Edimax unless you have that!
if you do so, or have done so, please refer to Troubleshooting KisMAC.
Kismac weak scheduling attack takes a long time
A Weak Scheduling attack may take some time, but you (yes, YOU) can make much faster:
Don't start cracking unless you have a mini of 130,000 IV's
200,000 is recommended
You may have collected corrupted packets, Sorry: S.O.L , try again
Rule of Thumb: The More IV's Collected, The Faster The Crack Will Be.
Another solution is to install Aircrack-ng: Collect packets (collect or re-inject) with KisMAC, Crack with Aircrack-ng: it's 10 X faster
How Many packets I need for WPA?
None! For WPA, you need to capture the Handshakes.
Look at the Ch/Re Gem indicator , or read the post related to that question.
How Many unique IV's for WEP?
Number of unique ivs needed kismac?
KisMAC: It is recommended to start at a minimum of 150,000 unique IV's
You can always try under, but it will probably fail or the key recovery may take much longer.
Aircrack-ng: As little as40,000 20,000
How fast can I successfully crack a WEP or WPA?
How fast can you crack a WEP key?
You just opened a can of worms ...
WEP
KisMAC: The more IV's you have collected, the faster the crack should be.
I have successfully cracked my own WEP key in less than 3 sec (128 bits key)
I also have, on the same key, spent hours with no success, .... I had up to 2 millions IV's
I suppose some frames were corrupted, but I can't say for sure. I made a Video on YouTube showing a crack in less than 3 seconds.
Aircrack-ng: 1 second on a 64 bit key with 40,000 IV's
WPA
It will depend on your password. If you use a dummy password*: between 5 sec and few hours.
If you use a GRC generated password, you better explain to your kids how to do it: they will continue your work long after you'll be dead. Seriously!
If you NEED an internet connection because you just moved, are in a new place, can't afford the monthly overpriced FIOS or UberDuper connection, then you'll need a SA-6p, SA-12PSA or SA-24PO
it's not software anymore, it's hardware, but I was successful in cracking a WPA2 in very, very, little time.
I have heard of BIM attack with Ha100B series, but I never tried it myself.
BTW: Dummy passwords: lists ARE available :-), I URGE you to use very serious password and avoid at any cost guessable passwords such as: 123456, 1234567, password, letmein, mustang, iloveyou, etc etc ...
PCAP Dump
When you check the box "Keep everything" it start saving a file where a bunch of details are kept.
This file is accessible for later review (advanced user only, please) you can use Wireshark to read that file and discover all the little tiny details ;-)
Console Log (from Console.app)
it's the log of what is happening behind the doors when you use your computer.
If you keep console log open, you may find messages such as "Warning, deauthentication Frame received"
It means that somebody is trying to penetrate your network with a Deauthentication attack. (more exactly, trying to force capture the handshakes)
KisMAC Tutorial
Resources
If you leave a comment or if your question is somewhat technical, please include detailed information.
KALI Reporter.app will do that for you!
Either visualize the report and post your system profile/info needed, or if you do not want the info to be seen publicly, just send the report via email. KALI Reporter takes care of everything. Please don't email your question.... post it on the blog. KALI Reporter.app will do that for you!
Troubleshooting KisMAC
KisMAC 0.3+ Bugs
KisMAC 0.3+ Issues
KisMAC 0.3+ Not Working
KisMAC 0.3+ Bugs, KisMAC 0.3+ Issues, KisMAC 0.3 Not Working
-Did you noticed that KisMAC 0.3 is for Snow Leopard 10.6 ? and not for 10.5? ok....
Can't Scan with KisMAC 0.3
"NOTE: If a previous installation of KisMAC has been used, please make sure to delete the following files, if they exist:" ( '~' is your home folder) (Using App Cleaner IS a GOOD IDEA)
- ~/Library/Preferences/de.binaervarianz.kismac.plist
- ~/Library/Preferences/com.kismac-ng.kismac.plist
- ~/Library/Preferences/org.kismac-ng.kismac.plist
Message
Could not instantiate driver. KisMAC has not been able to load the driver backend
Could not initiate driver. KisMAC has not been able to……

Whatever you do, if you have an injection device (WIFI card or USB Adapter)
DO NOT install the drivers of the card / USB adapter unless you have read this post
Possible causes:
You have NOT selected "Use As Primary device"
You Have NO Drivers selected
You have Selected the wrong one
Your Chipset is not supported (see Hardware list)
The Chipset of your USB Network Adapter is not correct (See FCC Number)
In order to avoid those issues => Best Wifi Card for KisMAC
If you look in your console.log (Spotlight >> Console)
you'll probably see a lot of lines with KiMAC as "sender" and an error messages such as:
KisMAC[2928] vendor 1452 vendorId 3574 product 32773 productId 38674
KisMAC[2928] Matching finished
KisMAC[2928] Error could not instantiate driver WaveDriverUSBRalinkRT73
Reading the last line, you can easily guess where the issue comes from: RT73 driver can't be loaded. Why? because you specified to KisMAC not to, or Specified to KisMAC to load the wrong one.Solutions
Select Appropriate Driver or use the proper USB Network Adapter. You may need to Force Quit the application
You have installed drivers provided with the CD of your USB Network Adapter.
Solution 1:Time machine? if you have Time Machine set up, pat yourself on the shoulder: smart guy!
If not, time to think about it and move onto Solution 1.5
Solution 1.5:
Uninstall the drivers* and the all shebang provided with your injection device
including the proper .plist for Kismac
use AppCleaner to remove all .plist
OR if you had a previous install, remove the following, if any:
~/Library/Preferences/de.binaervarianz.kismac.plist (where '~' is your home folder)
~/Library/Preferences/com.kismac-ng.kismac.plist (where '~' is your home folder)
~/Library/Preferences/org.kismac-ng.kismac.plist (where '~' is your home folder)
(told ya' use AppCleaner)
Solution 2: If, after uninstalling the drivers*, the problem persist, -and- you have trouble with your Airport Extreme, you may be in for a shitload.
Uninstall KisMAC, and re-install
Injection does not work
- Check that your device (USB/Card) is able to inject, => see Best Wifi Card for KisMAC
- Test injection: Tab “NETWORK” >>>”Test injection”

- Check that you have checked the box “use as primary device” in tab Preference >>> Drivers
- Check that you have the proper driver/chipset selected i.e. USB RT73 or USB RT2570 (Preferences >>>Driver)
- Check that proper channel is selected. One channel only: You cannot inject while Channel hoping is selected
- As stated, be very careful to have the proper chipset, otherwise: nada!
Word of advice, I would suggest you to test the hardware in a “brick and mortar” shop before you buy something that will not work, or take my word and experience for it, and purchase the best card available for KisMAC, it's less than $35 and allows you to get a signal up to 1 mile. it's 20x more powerful than an Hawking.
Reinjection Not Working
If you have tested the Re-injection and your card should re-inject packets, you may have the following issue(s)
- Your card is not powerful enough for the signal to reach the AP => get this one: Best Wifi Card for KisMAC
- There is not enough "good" traffic on the network. IV's (Initialization Vectors) are only about 5% of good traffic.
You also have the remote possibility to have encountered a very rare breed of APs: The one equipped with "WIPS" (Wireless Intrusion Protection System). In that case, Passive Mode is the solution.
If you want to know more, here is an excerpt from the KisMAC FAQ.
"What is packet reinjection?
802.11 requires frame retransmissions in the case of loss, so it may be possible for an attacker to retransmit a frame and replacement injected frame to be accepted as legitimate. Frames on wireless networks can easily be tampered with or forged outright, and the protocol does not provide a way to easily stop or even detect such attacks. Acknowledgment (ACK) and Address Resolution Protocol (ARP) are the management frames that are likely to generate responses from the client and APPacket reinjection is a very advanced WEP cracking technique. Be aware that this is the bleeding edge of technology, so it might not work every time. When you use this attack, KisMAC will try to find packets that will cause another computer to respond. The program will then send these packets over and over again. If KisMAC detects answers, it will go into injection mode..... Please be aware that all detections are of a heuristic nature, therefore it might not always be working"
Source: KisMAC
Packet collection is very slow
It’s probably because the network is not very active (low traffic). Just go on YouTube, watch few videos and the packet collection should increase very quickly.
Crack does not work
-Well, as stated in the FAQ, Injection is the bleeding edge of this technology, and I have experienced myself some failures with my own network: I was unable to crack my own key with more than 1,000,000 unique IV’s.
Other possible causes:
The key was changed during the collection
You have selected a 40/64-bit WEP when the key is 104/128-bit WEP, so in doubt, play safe and select both
You have encountered a SOL error: Shit Out of Luck
The wpa key could not be recovered because of the following reason:
the key was none of the tested passwords.."
Most likely, your dictionary file does not contain the exact password, read the article about wordlists.
WPA Reinjection Does Not Work
please note that RE-Injection and Injection are not the same.
-WPA RE-injection will not work, you can only RE-inject on WEP network, if you have an injection device. (i.e When you Deauthenticate , you are injecting frames)
KisMAC Crash on WPA Wordlist
KisMAC Can't Perform Injection Test
This is bug with KisMAC 0.3.3 while on 64-bit
Go to Applications >> KisMAC.app >> Get Info
Check "Open in 32-bit Mode" and restart.
Could not load Airport Driver
KisMAC could not attach to the Apple Airport Driver

This Error Can Have Multiple Origins, Please Read Carefully.
KisMAC could not attach to the Apple Airport Driver
In Preferences >>> Driver
You may not have selected any Driver (Apple Extreme, RT73, etc etc )and pressed the "Start Scan" button multiple times, this provokes a freeze and return this error.
The "Start Scan" button looks like the one in the picture below (button engaged)
The solution is a Force Quit and to select a correct driver in Preferences >> Driver
KisMAC could not attach to the Apple Airport Driver
Cause: Airport, Airport Extreme in ACTIVE Mode
This issue is fairly new and is related to the brand new Snow Leopard (10.6)
You have this error because you have selected Active Mode
Close KisMAC , re-open and select Passive Mode.
Do not use Active Mode with OS X 10.6 until further notice.
No Driver Selected
Please Select a WIFI Driver
Go back to Preferences and Select a Driver
i.e. Airport Extreme Passive Mode, USB RT73 Device, or else.
KisMAC Ch/Re Gem
The Ch/Re Gem is situated on the last column, right after "last seen"
Ch/Re stands for Challenge / Response
The Gems have 3 colors possible: Green, Orange and Red and the meaning will depends on the type of encryption of the Channel/Network

Enc = NO
The Network has no encryption (Open), (under column "Type") the Ch/Re Gem is green by default
Enc = WEP
The Network is encrypted by a WEP key, the Ch/Re Gem is red by default and indicates that Kismac does not have recovered a key (yet) No Challenge or No Reponse
Green Challenge or Response
Orange has a Challenge OR a Response
Enc = WPA
Red: No handshakes captured, don't even try a wordlist
Orange: Capture Started (?)
Green: Handshake Captured
KisMAC Freezes
KisMAC Hangs
KisMAC Freeze, KisMAC is hanging, KisMAC Freezes, PinWheel KisMAC
If KisMAC Freezes after few seconds, and hangs (Pinwheel) the first cause that comes to my mind is that you are using (listening to) the wrong channels.
If you are in USA, you should not be using Channels 12,13 & 14 (Europe and Japan)
If you are in Europe, You should not be using Channel 14 (Japan Only)
Just uncheck 12,13 & 14, that should resolve the problem.
Possible cause: Channels 12,13 & 14 are close to the microwave range and cordless phones (old ones)
It's possible that you are listening to your coffee or pop corn.
A second cause could be a large number of router using the same channels (often Ch 6), it may also create issues on your own network. In that case, just switch channels and you'll see an improvement in your Network quality
Can't Collect IV's
Can't Collect Packets
Packets Collection is very slow
I have received a lot of questions about this issue. The most probable cause is a non active network.
A non active or slow network (low traffic) is what makes the collection very slow.
KisMAC in passive mode is like trying to collect rain water: The more it rains, the more you can collect. That simple! If it does not rain .... or very little ... you got the idea!
A good wifi card will help you solve this issue
After receiving 10 + questions on the subject, here is an example of a near silent network:
As you can see 614,847 management packet (beacon) and only 25,945 Data Packets (the good stuff)
so, 615,902 junk.
This network is simply "on" but not used, hence, as long as there is no valid traffic, you need to be more than extremely patient
Other possible cause: You may be listening to a Probe, or a Router not connected to the internet, or someone that left his router on, but does not use it. Read the post till the end...
Here is what I have tested with active networks, and very active networks. It clearly shows that the collection of IV's is related to the traffic.
The test is with an Airport Extreme, Passive Mode, NO Re-injection
It took me 5 minutes to reach 130,000 IV on very active network, and 126 min on Active.
For the numerous persons that still believe that Kismac can not crack on Airport Extreme, the following is going to be surprising:
Very Active Network
Time : 0:02:05 2min, 5 sec
Bytes: 83.42 MiB
Packets 58,423
Unique IV in 0:02:05 = 57,016
U IV/Sec = 456.12
Theoretical Time to reach:
130,000 = 285 sec = 4.75 min
200,000 = 438 sec = 7.30 min
300,000 = 658 sec = 11.0 min
Active Network
Time 03:23:50 3hrs 23 min 50 sec
Unique IV's in 03:23:50 = 210,216
U IV/Sec = 17.18
Theoretical Time to reach:
130,000 = 126 min
200,000 = 191 min
300,000 = 285min
1 As Kismac has loaded the Airport Driver, he has control over it. Proof that this is on Airport and not on USB
2 Time
3 Packets
4 Unique IV's Collected with Airport Extreme on Passive Mode.
a Kismac still on Airport
b Time 2min and 5 sec
c Unique IV's Collected with Airport Extreme on Passive Mode. = 57,016 in 2 minutes, roughly 11 min to 300,000
d Bytes = 83.42 MiB for 57,000 IV's
Hence, Kismac does work on Passive Mode, and yes, you can crack on Passive mode without Re-Injection. If you can't, it's probably because of the network quality or simply because you may have selected a wrong parameter.
Test Your Own
One way to be sure is to test your collection speed:
Go to a friend's house , Start KisMAC , and ask your friend to watch multiple Youtube Video on its network. You want to push the router to the max.
You'll be then able to see if the issue is due to slow network or not.
While you're at it, ask your friend to run KisMAC too: You'll be surprised to realize that you can:
A) exchange PCAP dump files and try multiple cracks on multiple networks
B) if using Re-injection, notice that ONE device will make ALL Macbooks able to pick up the responses
Macbook does not detect edimax ew-7318usg
It's NORMAL! Don't panic!!!
Your Macbook can NOT detect your Edimax, because your driver(s) are not installed.
KisMAC will detect your edimax, under Preferences >> Driver >> use USB RT73 Device
DO NOT INSTALL the Drivers provided with the install CD of your Edimax unless you have that!
if you do so, or have done so, please refer to Troubleshooting KisMAC.
Kismac weak scheduling attack takes a long time
A Weak Scheduling attack may take some time, but you (yes, YOU) can make much faster:
Don't start cracking unless you have a mini of 130,000 IV's
200,000 is recommended
You may have collected corrupted packets, Sorry: S.O.L , try again
Rule of Thumb: The More IV's Collected, The Faster The Crack Will Be.
Another solution is to install Aircrack-ng: Collect packets (collect or re-inject) with KisMAC, Crack with Aircrack-ng: it's 10 X faster
How Many packets I need for WPA?
None! For WPA, you need to capture the Handshakes.
Look at the Ch/Re Gem indicator , or read the post related to that question.
How Many unique IV's for WEP?
Number of unique ivs needed kismac?
KisMAC: It is recommended to start at a minimum of 150,000 unique IV's
You can always try under, but it will probably fail or the key recovery may take much longer.
Aircrack-ng: As little as
How fast can I successfully crack a WEP or WPA?
How fast can you crack a WEP key?
You just opened a can of worms ...
WEP
KisMAC: The more IV's you have collected, the faster the crack should be.
I have successfully cracked my own WEP key in less than 3 sec (128 bits key)
I also have, on the same key, spent hours with no success, .... I had up to 2 millions IV's
I suppose some frames were corrupted, but I can't say for sure. I made a Video on YouTube showing a crack in less than 3 seconds.
Aircrack-ng: 1 second on a 64 bit key with 40,000 IV's
WPA
It will depend on your password. If you use a dummy password*: between 5 sec and few hours.
If you use a GRC generated password, you better explain to your kids how to do it: they will continue your work long after you'll be dead. Seriously!
If you NEED an internet connection because you just moved, are in a new place, can't afford the monthly overpriced FIOS or UberDuper connection, then you'll need a SA-6p, SA-12PSA or SA-24PO
it's not software anymore, it's hardware, but I was successful in cracking a WPA2 in very, very, little time.
I have heard of BIM attack with Ha100B series, but I never tried it myself.
BTW: Dummy passwords: lists ARE available :-), I URGE you to use very serious password and avoid at any cost guessable passwords such as: 123456, 1234567, password, letmein, mustang, iloveyou, etc etc ...
PCAP Dump
When you check the box "Keep everything" it start saving a file where a bunch of details are kept.
This file is accessible for later review (advanced user only, please) you can use Wireshark to read that file and discover all the little tiny details ;-)
Console Log (from Console.app)
it's the log of what is happening behind the doors when you use your computer.
If you keep console log open, you may find messages such as "Warning, deauthentication Frame received"
It means that somebody is trying to penetrate your network with a Deauthentication attack. (more exactly, trying to force capture the handshakes)
KisMAC Freeze, KisMAC is hanging, KisMAC Freezes, PinWheel KisMAC
Labels:
Aircrack,
Dictionary file,
Injection,
Troubleshooting,
wordlist
Subscribe to:
Posts (Atom)