
How to Crack WEP / WPA Step by Step
KisMAC for Dummies & Step by Step KisMAC Tutorial
KisMAC Tutorials for dummies, beginners & advanced users
Update of update : a Brand New Improved Video in HD, con la musica muy entertaining is available at the end of this post. it should cover KisMAC 101 and walk you trough WEP and WPA cracking
For the curious, advanced users and KisMAC geniuses , we have the following articles available:
Best Wifi Card for KisMac about 20 X more powerful than Airport or Hawking
Troubleshooting KisMAC
KisMAC Q&A
Cracking WPA with KisMAC
KisMAC Resources
KisMAC Deep Digging , Advanced Features
How To Install Aircrack On Mac
Before you post a question, PLEASE be sure to Read the 3 following post:
KisMAC + KisMAC troubleshooting + KisMAC Q & A
Once you are sure that the answer to your question can not be found, Please, Post your question in the Q&A Article: CLICK HERE.
ALL QUESTIONS WITHOUT KisMAC Version and OS Full Version will be ignored. Please Include Model and FCC number of the Network Adapter (the USB thingy) if applicable. And YES the FCC number is on it! and NO, it's not the MAC address.
Cracking WEP with Injection
Cracking WEP without Injection (Airport, Airport Extreme)
Cracking WPA
KisMAC Troubleshooting Guide
KisMAC Resources Dictionary file, Password list, etc
KisMAC is a free WIFI Network discovery tool and has a large array of powerful features: Detection, Authentication, Injection, GPS, and the ability to crack WPA & WEP keys.
KisMac is really powerful and leave Windows based NetStumbler in the dust. By a large margin.
Kismac is not for absolute beginners and the first step with KisMAC is to read the FAQ. The second step is to read the FAQ again.
Just a little legal warning:
- It is illegal to download, possess, and/or use Kismac in Germany, Austria, Switzerland and Lichtenstein (StGB § 202c)*
- It is illegal, in most countries, including the USA, to crack or attempt to crack, penetrate, listen to, intercept, or “Inject” any WI-FI network others than yours, or Networks where the unequivocal permission was not given to you by the rightful owner.
- Kismac is a tool that should be used on the sole purpose to check and/or verify, audit your own network
Now that I warned you :-) you can enjoy it!
Cracking WEP with Re-Injection
Whatever you do, if you have an injection device (WIFI card or USB Adapter) DO NOT install the drivers of the card / USB adapter.
DO NOT INSTALL DRIVERS FROM THE CD PROVIDED WITH THE DEVICE unless you have read this post
How to Crack WEP Step by Step
This tutorial is solely for you to audit your own network. I take no responsibility whatsoever, implied or not.
If you NEED an access, just ask politely your neighbor and either share the cost or discuss with him. A six-pack can be used as lubricant.
Cracking with Injection device

(Hawking HWUG1 shown here, RT73 Chipset. DO NOT BUY THAT ONE
Read review and comparison before: best card is here
Best Wifi Card for KisMac about 20 X more powerful than Airport or Hawking
The most successful method by far, with one little issue: you will NEED a Re-injection device: Either a USB WIFI Adapter or a WIFI card.
But, here comes the trick:
-You cannot use any WIFI card: You must use specific ones.
The list of “approved” hardware is here: http://trac.kismac-ng.org/wiki/HardwareList
As of today, you can NOT inject packet with your Airport / Airport Extreme Apple card alone.
Step 1
Download KisMAC from a trusted source such as: http://trac.kismac-ng.org/wiki/Downloads
Install KisMAC
Plug your Injection device, Whatever you do, DO NOT install the drivers of the card / USB adapter, or you may dearly regret it.
Start KisMAC
Step 2
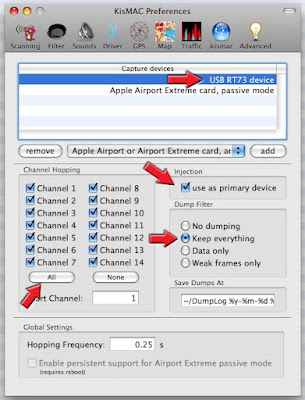
On the Tab KisMAC >>> Preferences >>>Drivers
Select your Injection device i.e. : “USB RT73 device”
If you have a doubt on what to choose, check the "approved" hardware list.
Click on “Add”
Check box “Use as primary device”
Select
In some Cases, Ch 12-14 can pick up interferences from other home devices: Stay within 1-11 !
Check box “keep everything”
Close Dialog Box
Step 3
On the main screen, select “Start Scan”
KisMAC is now listening to the accessible networks
Look for a network with a WEP key (column “ENC”), a good signal as well as traffic (see Packets and Data)
OR
Enter “WEP” on the search box (top right) and select “encryption” to filter the results
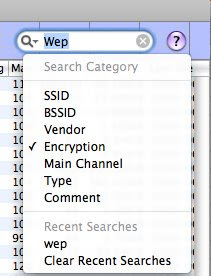
If the Column ENC is “NO”, the network is OPEN: No need of cracking anything
Once you have selected a network, look for the CHANNEL of the network, i.e 1, 2 etc …
Go back to Preferences >>>> Drivers
Select only the Network selected i.e 1
Step 4
Let KisMac work for 5 minutes collecting data
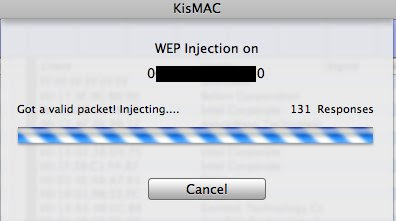
On the “NETWORK” Tab, select “Reinject Packets”
KisMAC will now try to reinject packets to speed up the process
Keep an eye on the “Unique IV’s” number, once it has reach at least 130,000 (200,000 is recommended) you may start considering cracking.
Step 5
Once you have collected enough, On the NETWORK Tab, Select “Crack” >>> “Weak Scheduling Attack” >>> “Against Both”
KisMAC will now try to crack the key…
Reminder: the more Unique IV’s you have collected, the greater are the chances to crack the key.
I have experienced crack as fast as 10 sec with 200,000 Unique IV’s (on a 64 bit key) and sometimes 30 minutes with only 110,000
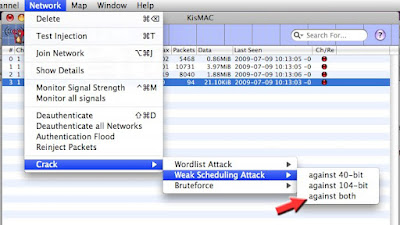
If you know for sure that the key is either 40 bit or 104 bit, then select the appropriate one. If you are not sure, select "both"
40 bit is a 64 bit (40+24)
104 bit is a 128 bit (104+24)
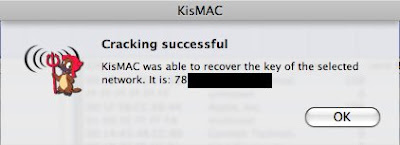
If you have followed the steps, you should see something like that appears :-)))
remove the semicolon, and there you have it, or take a look at the main screen under Key or ASCII Key
How to crack WEP / WPA with Airport Extreme, Passive mode
WITHOUT Injection Device (Airport, Airport Extreme Alone)
WEP attack
Step 1
Read the FAQ http://trac.kismac-ng.org/wiki/FAQ
Step 2
Read the “Newbie Guide” http://trac.kismac-ng.org/wiki/NewbieGuide
Step 3
Download KisMAC from a trusted source such as: http://trac.kismac-ng.org/wiki/Downloads
Last build is 0.3.3
Install KisMAC
Start KisMAC
Step 4 (without an Injection Device)
On the Tab KisMac >>> Preferences >>>Drivers
Select your card. (Capture devices) i.e : Airport Extreme Card, Passive Mode
Click on “Add”
Select Channels 1-11
Close Dialog Box, and select “Start Scan” on the main window
A dialog box opens and load the card. Your Admin password may be required.
Step 5
KisMAC is now listening to the networks accessible
Look for a network with a WEP key (column “ENC”), a good signal as well as traffic (see Packets and Data)
If the Column ENC is “NO”, the network is OPEN: No need of cracking anything
Once you have selected a network, look for the CHANNEL of the network, i.e 1, 2 etc …
Go back to Preferences >>>> Drivers
Select only one Network selected i.e Channel 1
Step 6
Be patient: open a beer, pour yourself a nice glass of wine or have a nice cup of coffee.
Without an injection device, you will need to collect a minimum of 130,000 unique IV’s before you can start cracking a 40/64-bit WEP
Recommended:
200,000 Unique IV’s for weak scheduling attack on a 40/64-bit WEP
1,000,000 Unique IV’s for weak scheduling attack on a 104/128-bit WEP
It may take a long time (based on: Network traffic, re-injection or not)
Those are recommendations. Weak Scheduling is basically a statistical attack: The greater the number of IV's collected , the greater the chances.
Are you in a hurry? : Capture with KisMAC, Crack with Aircrack-ng
You can have a successful recovery with as low as 21,000 IV's
Step 7
Once the packets are collected, Go to the tab “Network” >>> Crack and select the method,
For a start, I would suggest: “Crack” >>>”Weak Scheduling Attack” >>> “Against Both”
Once started, you’ll have to wait between 5 and 20 minutes depending on your machine for KisMAC to try all the keys.
The more packets you have collected, the better are your chances to be able to crack the key: The WEP Attack is Statistical, hence ....
WPA crack / Attack
>>>>> Packets RE-Injection DOES NOT WORK on WPA attack <<<<<<
>>> I said RE-Injection and not "Injection"
In order to crack a WPA key, you'll need the handshakes, a serious dictionary file or fileS and a LOT of CPU time. Hours and probably days of it. (read the "I am bored part" at the end)
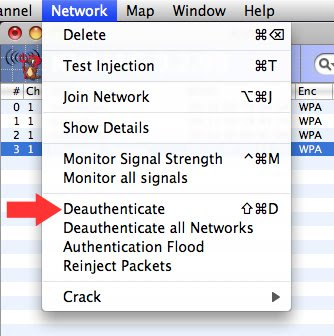
You first need to capture 4-way EAPOL handshakes (connection between the computer and the network) -When captured, you'll see the Ch/Re red dot turns green. You are ready to try...
To speed up the process of capturing the 4-way EAPOL handshakes, you can try a deauthenticate attack: it will force the network to shutdown and restart, hence speeding up the process.
Go to Network >>> Deauthenticate
Some network may recognize the attack and change channel.
Once the Ch/Re is ready, Go to the tab "Network" >>Crack >>WPA
It will then ask you for the dictionary file, select the file you want to use, and start...
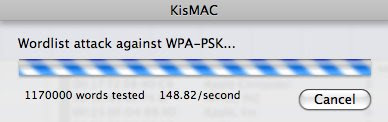
Nota Bene:
KisMAC will try every word (from the list provided) to attempt to crack the key, hence it may take a lot of time....if you have a slow machine, be really patient.
I have a not so bad machine, and I run about 170 words per second. You can leave a comment with your config and speed for me to compare.
Mine: MacBook Pro 2.5GHz Intel Core 2 Duo + 4GB DDR2 SDRAM : about 170 Word/sec
As for the Dictionary files, you can find links on the KisMAC website or take a look at the "RESSOURCES" post.
Note on dictionary files:
Wordlist = dictionary file
- The words are tested "as is" and not in combination.
Example: the password is "I love Kismac"
If your dictionary contains the words "I" + "love" + "Kismac" it will NOT work, your wordlist must contain the exact (verbatim) "I love Kismac" as a word to successfully attempt to crack.
The files must be a text format .txt and contain a empty line at the end.
KisMAC Troubleshooting Guide , KisMAC Issues, KisMAC Ressources are on the NEXT post....
KisMAC for Windows, ditto...next post
WPA: Wordlist links and files Download are here







Nice tutorial!
ReplyDeleteWhat does the color of the circle under Ch/Re mean?
Does green mean it's ready to crack?
It depends on type of encryption:
ReplyDeleteNone or Open: Green by default
WEP
red: undefined key (not cracked)
Green: Defined key (cracked)
WPA
red: Handshakes not captured, no need to try to crack
green: Handshakes captured, you can try to crack
Hi,
ReplyDeleteNice blog, at least smtg clear to understand how to use kismac, great thx.
Anyway I got a pbm to get a wpa key.
I got the data packets ok, I get the green light with the deauthentification, but when I ask to find the wpa I get this:
"the wpa key could not be recovered because of the following reason: the key was none of the tested passwords.."
Thanks for the cheers :-)
ReplyDeleteI have posted a detailed video on Ytube,
http://www.youtube.com/watch?v=lBGN5OGCPgI
I will post soon dic files.
Re: "the wpa key could not be recovered because of the following reason: the key was none of the tested passwords.."
it's probably because your dic file does not contains the exact (verbatim) pswd
KisMAC does not use a "real" Bruteforce attack to crack WPA, but a bruteforce on a list.
Take a look at the "nota bene on dic file"
Using real Bruteforce (a,aa,aaa,aaaa,...abaaa, etc) would be un-human and you'll be dead long before cracking a 10Ch ASCII.
Read the "I am bored" part for an idea of how long it may take...
Where did you post the dictionary files?
Deletehttp://easymactips.blogspot.com/2009/11/support-donate.html
Deletehttps://wiki.skullsecurity.org/index.php?title=Passwords
DeleteWow! I am impressed!
Delete2 GB of data. Do you want 100GB? Please, let me know how it works for you, specially with your WEP.
But hey, you have saved $5 and lost 50 hours of useless computing.
Congrats!
Hi ! Very very nice blog !
ReplyDelete2 questions :
- to crak wpa key what kind of USB device i need ? (name please)
- what does mean dictionnary file !??!
Thanks a lot !
Hey,
ReplyDeleteThanks for the comment.
All answers to your questions are posted in the second part of the post, look in Resources and Troubleshooting.
Read carefully the WPA part as it can be a long process to crack a WPA key.
dictionary files are also known as wordlist
Don't use kismac to crack your handshake. If it writes it to PCAP format as it should, you should be able to get about 300 keys per second out of it (I can do so on a 2.2 intel dual core with 1GB of RAM).
ReplyDelete"Don't use kismac to crack your handshake"
ReplyDeleteSorry, I am not sure I follow you.
we're talking WPA here, correct?
According to KisMAC, the only way, with KisMAC to break a WPA is to use a wordlist.
Handshakes or 4-Way EAPOL are not cracked, they're captured. The Deauthenticate attack speeds up the process of D-auth.
If you have another solution(with KMac) please let me know in details,I'll be really grateful
WEP: between 1000 and 3000 key per second
Hi I have some problems to find Kiss Mac Dictionary files. can you post a link please.
ReplyDeleteThanks
Hello Sergio,
ReplyDeleteThe Wordlists, or Dic files are posted here
http://aloah.free.fr/Mactips/home_En.html
you'll also find a builder or expander to create larger Wordlist
It was explained in the "resources" section.
When using KisMAC, you should familiarize yourself and read the FAQ and troubleshooting before. A lot of things can go wrong and you will save a great deal of time
I Unfortunately installed Ralink Rt-73 USB driver via CD~ BEFORE~ I intalled Kismac. So Kismac recognizes it but will not connect to it in Preferences. Should I uninstall USB wireless utility, removing all traces in the preference panes and start over? once uninstalled should I be able to simply plug in my USB device and Kismac will now connect to it?
ReplyDeleteyup,
ReplyDeleteUninstall thoroughly everything you have installed via the CD, or better, use your Time Machine.
take a look at the post "ressources" for KisMAC, you should find some info.
If not, look into the console log.
Also, KisMAC should return an error, please indicate what type (for a better debugging)
hi there, congrats for the nice job here....
ReplyDeletei woud like to ask you if on a MBP I get a usb device rt73 Hawking HWUG1 for ex, do I need to install subversion, xcode and compile kismac explained on this link?
http://screammy.name/projects/kismacmacbook/
I really hope not.... :)
Will you advice me about the USB devise "rt73 Hawking HWUG1 "and "rt73 Hawking HWUG1A" , whats the diference between them and your opinion about this USB DEVICE "D-link DWL-G122?
This blog will be from now on my favorites...
Thanks in advance and keep the good work
J
Hi J,
ReplyDeleteThanks for the cheer up.
I have posted a reply on the Q&A part of the "Troubleshoot" Kismac
(Few posts down)
Thanks for your repy,...really appreciate.
ReplyDeleteIm gonna try the usb AWUS036s, but I see also that Alfa got a usb AWUS036H device, more powerful..., is it also compatible with kismac 0.2.99 ?
http://www.data-alliance.net/-strse-73/802.11g-USB-802.11b-high-dsh-power/Detail.bok...
Ive got a MBP 2.4 Ghz Intel core duo with 4 Go 667 DR2 SDRAM
Thanks in advance :)
J
Have you read the post(s)?
ReplyDeleteHey!
ReplyDeletegreat blog, I learned more that just cracking wep keys. I just have one question: where do I enter in the wep key to gain access to the network? I'm a silly newb so after I got the key I simply clicked on the wifi icon on my toolbar and entered in the 14 character wep key which failed to connect to the network. Obviously I was totally wrong in doing that so where am I supposed to enter that key?
Thanks =)
Wifi icon on toolbar:
ReplyDeleteThe Airport icon?
you just need to enter the ASCII key in the appropriate network
If you enter the Hexadecimal Key, don't enter the semicolon
i.e 12:45:34 would be 124534
This blog rocks! I actually was able to find a Linksys router at one of my employee's desks by tracking the MAC address in our network monitor. Killer tutorials.
ReplyDeleteI have one question though. There is a network that I can't seem to crack. It's using WEP but the channel keeps changing. Does kisMAC support this or is there a workaround?
Thank you for all the time you've put into this!
To Anonymous
ReplyDelete"There is a network that I can't seem to crack. It's using WEP but the channel keeps changing."
Are you using a passive mode or using re-injection?
It's possible that, if using re-injection the router detects it and change channel. it's rare but it can happen.
Try both ( passive and re-injection) and see if you detect a change.
Console.app may give a hint (not sure though)
I've tried both passive and re-injection mode. I can actually see it change channels in the "show networks" window. The device is listed as a Netopia and I see from the details that the main channel is 6, but it bounces around to 4, 6, and 8.
ReplyDeleteOh well... I guess you can't break them all... :)
Thanks for your quick response by the way...
It's strange that is bounces on passive. Do you know if it is a very dense network grid?
ReplyDeleteGo to the Q&A, look at the end of post, and send me the Network, MAC address, etc by email. I'll look if I can find something
hi, nice tutorial, but i still cant get it working. I am trying to crack my own network(WPA). I have usb wireless stick i found network, get green light on ch/re, try to crack it with dictionary file but i get message that network couldnt be cracked because password doesnt exist in the file. I put my own password in the file so it has to be found. Help please?
ReplyDeletemismac:
ReplyDeleteI think it is already answered:
File must be .txt and contain an empty line at the end
Passwords are tested "verbatim"
Hi there, first of all, great guide!
ReplyDeleteI've got Kismac .30 installed on a Mbpro running 10.6.2, and got hold of a RT73-device (Edimax ew7318usg) (and haven't installed any drivers) I'm trying to gain access to my own (naturally) wep-encrypted network, but when I've collected about 100 unique IV's and i select "reinject packets" nothing happens, except it seems to be counting down through my IV's but not getting any responses, thus not generating more.
...I can of course just scan longer and wait passively for several hundred thousand Iv's, but I'm just wondering: Are there "good" Iv's and "bad" ones, or why are there no responses?
Regards!
Morten,
ReplyDeletecollecting packets is like collecting rain water, the more it rains, the more you collect...
If the traffic is slow, you can wait a long time for a good packet to re-inject.
So, when RE-injecting, you have first a "Waiting For Interesting Packets"
(look a the video, 04:34)
To Speed up the process, just go on youtube, and rewatch the video. (Awaiting for a Grammy) During that time the traffic will likely increase and you'll get a bunch of "good packets" to re-inject.
You can also look at:
http://easymactips.blogspot.com/2009/07/kismac-ultimate-stumbler-ressources.html
and read the "Can't Collect IV's" part. it's pretty straightforward ;-)
Hi,
ReplyDeleteI have MAC OS X 10.6.2 and KisMAC 0.3
I have found the WEP
I have 250.000 Unique IV's
I went to Network/Crack/Weak Scheduling Attack/against both
Now it's written Weak Scheduling Attack....
Checked 3500,000 and it is still going
Why can't it find the WEP key?
Raffi
ReplyDeletehttp://easymactips.blogspot.com/2009/07/kismac-ultimate-stumbler-ressources.html
Hello!
ReplyDeleteI installed the 0299 version of KisMAC on the 2008 iMac, I found a WEP network (do not know if at 64 or 128 bit), I've been collecting IVs (about 500,000) but when I make a weak scheduling attack, is still the same key does not work (ASCII key 5 characters). I had already tried it with 130,000 and with 200,000 as recommended but the key is always the same and does not work!
You recommed me waiting 1,000,000 or 2,000,000 IVs or start again? May have caught handsnake corrupt? Must decrypt the ASCII key in hexadecimal key?
Please Help me! If you want I can post pictures ... bye
Anonymous,
ReplyDeleteLook at the previous post for Raffi, same issue.
>> Handshakes are for WPA
>> Re-start again , if you get the same key, the problem is somewhere else
>> Hex key must be entered without the semicolons
>> ASCII key must be entered verbatim
Hello.
ReplyDeleteI wanted to know why when I try a weak scheduling attack at two different times (about the same number of IVs) the first time out immediately the ASCII key while at the second attempt began to test all the keys, etc. 1000 2000 3000 and employs a lot time.Why?
Bye
I suppose the answer rest in your question:
ReplyDelete"(about the same number of IVs)"
Hence, not the same IV's
Use the same PCAP file (dump file) and you should have the same results all the time
Hi there
ReplyDeleteIt's my first time trying to crack a WEP encrypted network. Just moved into a new apartment and there are 20 or so nearby networks taunting me, all encrypted (most WEP, I won't bother with the ones that have WPA encryptions.) I'm collecting data packets from the three networks with the best signals.
With one of the networks I have collected nearly 2.5 million data packets, with only around 69K unique IVs whereas one of the other networks has only around 1million data packets and already 110K unique IVs. Any idea why this is?
Anyway, tried cracking the network with 110K unique IVs last night, left it running for a few hours to no avail. Any idea where I could be going astray? Should I wait for more unique IVs and try again?
Thanks,
Christina
Christina,
ReplyDeleteI do not condone, help, or promote illegal activities.
you seriously need to read the legal disclaimer: cracking an "unauthorized" network is a crime, and by helping you, I would be also under the long arm of the law.
I suppose you would not appreciate your neighbors doing to same to you.
If I were to crack your network and penetrate your computer, you'll probably be furious against me.
Nevertheless, if you want to succeed, read the part that mention:
"If you NEED an internet connection because you just moved, are in a new place, can't afford the monthly overpriced FIOS or UberDuper connection, then you'll need a SA-6p, SA-12PSA or SA-24PO"
it's right here in this blog, under Troubleshooting'
Good luck
Oops, I'm sorry- too much information, I should have known. But thanks for the tip.
ReplyDeleteHi. I have followed all of the instructions, but I can't seem to get KisMAC to scan in passive mode. I have a new MBP6,2 with Core i7 and AirPort Extreme (0x14E4, 0x93) Firmware Version:Broadcom BCM43xx 1.0 (5.10.131.14.7). When I hit the scan button, I am asked for my password, which I enter, but after that, nothing happens (ie - no scanning). Thoughts on this? Thanks.
ReplyDeleteNew MBP 6.2 ??? You need to send me that beast ASAP (for me to conduct some scientific test, research purpose only :-)
ReplyDeletea ) check that video , step by step
http://www.youtube.com/watch?v=Pyiz2Mct6dk
be sure to hit "scan" and to have the proper settings for your Airport = Passive mode
Also , KisMAC 0.3??? First Install?
Let me know ....
Yep, doesn't work. Nothing. I hit Start Scan, and it responds (ie- the button IS pressed, but then nothing. No scanning, no info gathered,nothing.) I'm not a newbie, so I'd like to think I can troubleshoot, but not on this problem. I feel it must be obvious, I'm just missing it.
ReplyDeleteBTW, 0.3 was my first install.
Check the Console.app for any weird message.
ReplyDeleteIf you have growl, you should see a message "KisMAC Scan Started"
If you have correctly selected the capture device , Apple Airport Passive Mode" and it's not working, then the last before calling god is iChat + Screen Control.
Shoot me an email ...
email link is in
ReplyDeletehttp://www.google.com/recaptcha/mailhide/d?k=01UYrcOb9KW7S1kLXrqN6IKw==&c=KcRwiSDknB1ieUnMh8dINA==
Hey just writing on the blog like you asked ;) Yes this is my first install with KisMac 0.3 there was no .plist in the prefences folder related to kismac and I am correcting what i said to you before... There is no crashing I am able to scan except it is extremely slow almost to slow that the program is impossible to use and the thinking wheel is constantly spinning. Here is my information again...
ReplyDeleteSnow Leopard - 10.6.3
KisMac - 0.3
Network Chipset - Card Type: AirPort Extreme (0x14E4, 0x8D)
Firmware Version: Broadcom BCM43xx 1.0 (5.10.91.27)
And here is what I pulled from the console...same errosr over and over again until I quit..
10-05-27 7:45:10 AM [0x0-0x9c09c].org.kismac-ng.kismac[1136] 1_ERROR_DOMAIN Code=-3900 "The operation couldn\u2019t be completed. (APPLE80211_ERROR_DOMAIN error -3900.)"
10-05-27 7:45:12 AM [0x0-0x9c09c].org.kismac-ng.kismac[1136] Error Domain=APPLE
10-05-27 7:45:12 AM [0x0-0x9c09c].org.kismac-ng.kismac[1136] 80211_ERROR_DOMAIN Code=-3900 "The operation couldn\u2019t be completed. (APPLE80211_ERROR_DOMAIN error -3900.)"
10-05-27 7:45:16 AM [0x0-0x9c09c].org.kismac-ng.kismac[1136] Error Domain=APPLE8021
10-05-27 7:45:16 AM [0x0-0x9c09c].org.kismac-ng.kismac[1136] 1_ERROR_DOMAIN Code=-3900 "The operation couldn\u2019
10-05-27 7:45:16 AM [0x0-0x9c09c].org.kismac-ng.kismac[1136] t be completed. (APPLE80211_ERROR_DOMAIN error -3900.)"
10-05-27 7:45:16 AM KisMAC[1136] DEAUTH ALL 0
b_basler
ReplyDeleteSeriously, have you looked for any info on this page?
Try a Command + F or Google your error "80211 ERROR DOMAIN Code=-3900", that will return :
http://easymactips.blogspot.com/2009/07/kismac-ultimate-stumbler-ressources.html
Why do I see DEAUTH, are you trying to DE-authenticate?
Are you in your kitchen or in a dense WIFI Area?
Once you have thoroughly read the previous answers, If that does not work, I need full config, including Mac, memory, apps running, etc
If you run kisMAC with no memory left on a G5, I can't guess it.
Heh ya I did read that and I didn't choose channels 12 13 14 and what do you know it works :) I don't understand why having those selected would cause it to slow and freeze at times. No, im not in my kitchen im in my basement so not a dense wifi area. Thanks for your support!
ReplyDeleteChannels 12,13,14 are not used in the US. Only Japan uses 14
ReplyDeleteOn those ranges, you are close to the range of Micro Waves Oven, Baby Monitors or cordless phones, they can "pollute" your WIFI connection. When in dense WIFI area, the same can happen when too many are on the same channel.
So I guess, I was not sure before if it was the cause, now it's getting closer.
Sorry, im just a newbie.
ReplyDelete1. Using your tutorial how to crack WEP with injection device (in this case im using Asus WL-167G v2) RT73 chipset. I was curious, what for we doing reinject packet? When i was using reinject packet, theres something written on it "got a valid packet" injecting... and the right place theres a number or response. The question is, how long should i wait for the injection finish?
you said that "KisMAC will now try to reinject packets to speed up the process" but the question is, when i reinject packet, how come it speed up the process but the injecting never finish/done (question 1), OR it can FINISH? but in my case, i have waiting the reinject packets finish, but over 6 hours the reinject packet still there, not finish/done.
3. is reinject packet has affect with the unique IV?
4. just said that i have collected enough unique IV about 200.000, should i turned the scanning off for doing the next step (against both).
5. if i collected unique IV without injecting, still i doing crack WEP using RT73 and against both option?
6. What is different between 40bit with 104bit?
7. Which one cracking is the quick one? And why you said that quick? what reason?
8. What for doing test injection if you already know that your tools can doing injection and the method you want to use is injection method
9. Sorry, im just curious. I already read the TSG (troubleshooting guide), FAQ etc but i cant find the answer OR i understand the meaning.
sorry for my english. Im using MacBookPro 2009 earlier with SL 10.6.3, cracking tools is Asus WL-167G V2. the methode i want to using is cracking WEP
- The question is, how long should i wait for the injection finish?
ReplyDeleteUntil you reach a minimum of 130,000 IVs
KisMAC will re-inject packets for as long as you keep re-injection active.
3. is reinject packet has affect with the unique IV?
- Short answer: Yes.
4. >> yes
5. >> yes, it's called passive mode.
6. Length of the encryption. 104 is "more secure"
7. If the encryption is 104 and you try to crack it as 40: Good luck!!!
8. Test means "test". it's a "TEST", hence not mandatory
9. You can Google a little and read, it seems to me that you are very confused on what does what. i.e "cracking tools is Asus WL-167G V2" or even 40bits Vs 104.
Your Asus is not a "cracking too" it's a Network Adapter"
it only transmit data.
hello. You seem to be the man to talk to!
ReplyDeletei have a few questions for you.. hope you can help.
i have a macbook 10.5.8 2.4 GHz intel Core 2 Duo
2GB 667 MHz DDR2 SDRAM
loaded kismac 0.2.99- check
preferences- Apple Airport extreme, passive-check
scanning check
correct channel picked -check
dont have a external usb driver- so i'm doing it without injection.
network signal is strong for particular WEP, data being received packets also- the prob is no IVs-? it remains at zero..
now heres my question- can i crack network with just packets and (No) IVs !!??? do they both have to be in the hundreds of thousands at the same time for the crack to work like you wrote (read alot of your info..maybe i missed another blog)?.. also... getting the packets is tremendously slow and slow IVs on other networks.. been scanning for over a hr and only have 18,000 packets so far as a example of slow...IVs also still at zero...(is there a way to get the IVs going?) as it goes for most of the networks also.... on other networks that i see.the most IVs i got is less then a thousand as the highest out of all of them..and thats in one hr...if i need 150k to 200k as a average...then doing the math at this rate...150 hrs of collecting??? wow has to be a better way!!
note- i noticed before the channel rapidly changing on the particular network..but now holding the same channel primarily at least for the last hour...
any advice would be appreciated
Your answer is here:
ReplyDeletehttp://easymactips.blogspot.com/2009/07/kismac-ultimate-stumbler-ressources.html
Can't Collect IV's
Can't Collect Packets
Packets Collection is very slow
I fear I am probably running into an ID: Ten-t error, but I have been reading enough and not finding an answer so I am unsure that is all that it is.
ReplyDeleteA friend of mine taking a class in Internet security and told me about kismac, and I have learned much about how it works (and how often it doesn't) by playing with it and reading the various faqs and tutorials.
I have set up both a linksys and a 2wire routers, both with 40bit keys (and both on channel 11 so I can collect packets simutaniously). But I have been unable to get the packet reinjection to bear fruits. I am using an awus036H USB adapter, and I can successfully do a test injection (the first 5 or so gems turn green) and I can seemingly inject packets, but I have yet to get a respose from either router.
I also have a question about authetication floods. The best description I have seen describes it as a flood of authentication requests, in the hopes of getting a responce that reveals part of the encryption key. If that is the case does that mean that this is another way of collecting unique IVs?
Thanks for putting together such an awesome collection of information. I plan on working my way through most of the rest of your blog over ne next week as things like this fasinates me.
No ID10T error so far, but, try put yourself in my shoes:
ReplyDeleteIf I were to ask you a question such as "My car does not work, what should I do?"
What would be your first question back to me? Make? Model?
Same here. Otherwise I can assume that you have Win95 and KisMAC Trunk 0.01
The Second thing is: try to ask your question in the Questions and Answers Article : http://easymactips.blogspot.com/2009/09/kismac-q.html
Thanks
Dude props, this is the best unofficial user guide i have ever read.
ReplyDeleteQ: up to how long would a weak scheduling attack take with 200,000 unique ivs, using the HWUG1A, os x 10.6.4?
Brandon:
ReplyDeleteAnswer & proof documented here:
http://www.youtube.com/watch?v=qHHLI__xhY0
Private tutorial ?
ReplyDeletethanks
Private tutorial:
ReplyDeleteContact me here for details:
http://www.google.com/recaptcha/mailhide/d?k=01UYrcOb9KW7S1kLXrqN6IKw==&c=KcRwiSDknB1ieUnMh8dINA==
I try to find the proper place to post my response but I could not find it, therefore I need some help on how to work my adapter with KisMac. I recently bought a HWUG1 Hawking USB adapter with antenna from an ebayer, the problem is, when I try to work this thing with Kismac I select the RT73 preference for USB, but it gave me an error showing the following:
ReplyDeleteKisMAC was able to load the driver backend for USB RT73 device, but it was unable to create an interface. Make sure your capture device is properly plugged in. If you think everything is correct, you can try to restart your computer. Maybe your console.log and system.log show more details.
How do I fix this? I am using Snow Leopard 10.6 OS X, in brief the >$2000 17-Inch Macbook Pro. Dang this computer is supposed to be good but what the heck?
The main goal I am trying to do is WEP cracking, I saw videos on youtube but they don't have the specific case in which I have. Anyone can help that would be much appreciated.
Thanks
Hulei,
ReplyDeleteAs indicated in this article, in regards to the Hawking:
"(Hawking HWUG1 shown here, RT73 Chipset. DO NOT BUY THAT ONE"
The solution to your issue is here:
http://tinyurl.com/37x6bhv
Would there be a reason that I am not collecting any Injection Packets? It always stays at 0, so I can not reinject them to get more unique IV's.
ReplyDeleteAny help would well..... help :-)
has anyone tried to use Parallels or Vmware fusion running on OSX to try all of the Linux WIFI-crack tools. Is it doable o not?
ReplyDeleteHello,
ReplyDeleteI have Macbook pro 2.4 GHz Interl Core 2 Duo with Snow leopard 10.6.6
I bought the HAWKING HWUN3 " white " for mac , at the begining I installed the driver that comes with the HAWKING, then I saw your video and I removed the driver with the uninstall utility that comes in the CD.
I download all versions of KisMac and none worked for me, your help is highly appropriated .
Fadyi,
ReplyDeleteYou NEED to read a bit more. it's explained 10 times on this blog that you MUST NOT INSTALL THE DRIVERS.
Un-install the Hawking drivers, and retry.
Also, if you can return the hawking, do it now. it's a piece of junk.
Read this article: http://kismaxx.blogspot.com/2008/11/kismac-best-compatible-wifi-card-re.html
The problem I found out about your blog , after I did the installation . I managed to uninstall the drivers.
ReplyDeleteIt will cost me more to return the Hawking card, the funny thing is that this card was recommended on another site to be used with Macbook and Kismac.
Fadiy,
ReplyDeleteWhich website?
The white hawking is the same as the grey one. Chipset is the same, spec are the same.
The only difference is the software, that you can not use(!)
The Card that I recomend is cheaper than the Hawking and has 8 times more juice. If you can get a signal 3000ft away with the Hawking, I'll buy you a drink.
it's explained in details here:
http://kismaxx.blogspot.com/
If your drivers are properly un-installed, KisMAC should be running with no issues.
Im using KISMAC 0.3.3 and TL-WN321G on RT73 device. Everything looks correct, but I CAN´T reinject packets because appears NO SSID or HIDDEN SSID.
ReplyDeletequestion already answered
ReplyDeleteWhat of Adapters that function also in the "n" networks?
ReplyDeleteHi everybody,
ReplyDeletethis blog it's great!!
I'm just a beginner on KisMAC and I'm trying to crack my own network with WPA... but I've a question that I've no read in the Q&A: how long it takes for a deauthentication attack? I mean how many hours, more or less. Because after 3/4 hours the handshake dot is still red...
Thanks for any help!
between 5 sec and eternity.
ReplyDelete"Step 1:
Capture the 4way Handshake
Before doing anything, you need to capture the handshake between the AP (Access Point) and the Client. The handshake is sent when a client connects to the AP. This process of "listening" to the AP-Client can take some time. In order to speed up this process you can use a Deauthentication Attack. The Deauthentication is a bit like a Ddos and will simulate a "kick out"and force the AP to respond."
...got it!
ReplyDeleteit seems that I'll have to be more patient ;)
thank you so much
if you make a connection, the handshakes will be sent again. use airport ..
ReplyDeleteHi everybody,
ReplyDeleteI'm still the last "anonymous"... first of all, thankyou so much for your help!
But now... 2 more questions!
1. Once I get the handshake and launched the wordlist attack, kM suddently crash/stop after few seconds. Why did it happen? (worlist are .txt and with empty line at the end)
2. May be due to the fact that I've to stop scanning before launching wordlist attack? I think to have read something, but I don't find it anymore!
kM 0.3.3- MB 2.2 Ghz - Mac OS X 10.6.3 - AWUS036H
Any help will be appreciated!!
=> A bug in KisMAC 0.3.3 prevents from using a wordlist on a WPA key recovery while on 64-bit
ReplyDeleteEither, Select the 32-bit option on "Get Info" on the KisMAC.app (Finder >> Applications Folder >> KisMAC.app >> Get Info)
Or use KisMAC 0.3.2, 0.3.1 , or even better: Aircrack-ng
=> http://easymactips.blogspot.com/2010/10/how-to-install-aircrack-on-mac.html
Yup, a lot of anynymous, you guys should use pseudos: that will make the comments more readable :D
Good morning, I bought the ALFA AWUS036NEH 150Mbps and when I plug it to my MacBook Pro 10.6 Snow leopard, it does not recognize it. I install the driver ONLINE due to the fact that the box came with a mini DVD and MAC do not like these, as they get stuck in the DVD device, so I went to the ALFA site and download the correct driver for 10.6
ReplyDeleteNOTHING!!! Still not recognizing the drive or the chipset when plugged in, I am trying to use Kismac and I always get error messages like:
Could not instantiate Driver.
KisMAC was able to load the driver backend for USB Prism2 device, but it was unable to create an interface. Make sure your capture device is properly plugged in. If you think everything is correct, you can try to restart your computer. Maybe your console.log and system.log show more details.KisMAC was able to load the driver backend for USB Prism2 device, but it was unable to create an interface. Make sure your capture device is properly plugged in. If you think everything is correct, you can try to restart your computer. Maybe your console.log and system.log show more details.
No injection driver.
You have no primary injection driver chosen, please select one in the preferences dialog.
Please help !!! Thanks...
Dear anonymous,
ReplyDeleteIt's the morning here. I was having a nice cup of Joe when I read your post: I almost barfed the coffee on the screen!
Presently my co-worker is banging his head on the desk.
You have *OBVIOUSLY* failed to read ONE single line of this blog. You can't possibly have tried.
If you need personal tailored assistance, for any reason, including because you do not want to be bothered and wish to be able to use KisMAC like a pro, We have the KisMAC School. It's the best help you can get.
it's here:
http://easymactips.blogspot.com/2009/11/kismac-school.html
Admin,
ReplyDeleteKisma 0.3.3, Alfa awus036h, mac osx 10.6.8.
Trying to reinject on my wep.
1) I am really just wondering, when i do a test injection it just hangs and waits, nothing populates in the boxes is this normal for a slow network? Also when I actually perform a re-injection on the wep network, it just creeps along. Is this truly just due to the lack of activity on the wep network?
2) Also I thought re-injection sped up this process regardless of traffic on the targeted wep network, or am I misunderstanding.
3) Finally, does re-injection only speed up when there is normal traffic and not when there is hardly any?
Thanks for answering the questions, I have been reading the blog, and saw that this takes time, I also checked everything on the AWUS usb and it is a legit model.
Thanks again,
Vincent
Vince,
ReplyDelete1) "is this normal for a slow network?"
No, Slow or not, the injection TEST should work. It tells you that everything is in order to work, and the (actual) speed of the network.
2) "Is this truly just due to the lack of activity on the wep network?"
-Mostly. Try to open multiple youtube video to maximize the traffic on the network. You should see the data flying up. Then Re-inject.
3) "only speed up when there is normal traffic and not when there is hardly any?"
Re-injection is made to artificially increase the # of IV's. Once Re-injection has started, the amount of traffic will have very little impact.
Admin,
ReplyDeleteThanks for the quick response.
In reference to my first question any thoughts on why injection/reinjection wouldn't be responsive for the test?
And i begin an authentication flood, not sure if this increases traffic, and next begin re-injection after i have some iv's and packets, when i am re-injecting i do get 200 or so responses, it just seems minimal to other examples online, including yours, I have seen.
Any other additional feedback is appreciated.
Thanks again,
Vincent
Why use a DE-authentication? the network is not hidden, is it?
ReplyDeleteAs previously explained in the blog, de-hauthentication forces the AP to re send the authentication frames, hence de-cloaking. it may (possibly, sometimes, not sure, it depends) force an ARP , but that would depend on the router.
http://easymactips.blogspot.com/search?q=deauthentication
On the top of that, when using deauth, you leave the cover of stealth and become visible. FYI, I could detect you, counter your attack, and locate you very precisely.
" do get 200 or so responses, it just seems minimal to other examples online"
the pop-up window says "received 200 responses, re-injecting" ?
In that case, re-injection is working. Working very well as a matter of fact. You just need to let KisMAC re-inject enough IVs. Re-injection is NOT instantaneous.
Admin,
ReplyDeleteThanks again for the feedback.
It was my misunderstanding of the flood as a de-authentication technique. I understand your statement now.
Also for the reinjection I was just puzzled why the test woulf fail, then when I would try the normal reinjection I come back with responses. I have roughly gained 40k ivs over 3+ hours of listening and reinjection.
Finally I guess my questions stem from whether this timeframe is normal when trying to snap a wep with little traffic in your experience.
Again, truly do appreciate the feedback and help with learning this tool, sorry any perceived ignorance I display.
Thanks again,
Vince
"I was just puzzled why the test woulf fail,"
ReplyDeleteThat, I need to see in details. i.e Quicktime. + Console log.
"..timeframe is normal when trying to snap a wep with little traffic in your experience"
Yes, but as it is your network, I clearly stated to open multiple YT to boost the traffic. The more traffic, the better.
"Again, truly do appreciate the feedback"
No problems, everyone has to learn one day.
It's just when people show a strong belief of entitlement coupled with rudeness and the spelling capabilities of a lolcat, then, I must admit that the answer is not that... nice.
have a good one.
Admin,
ReplyDeleteOne last quick question, what is your preferred loadout, which version of Kismac do you utilize or is it a combo of aircrack and kismac?
Thanks again,
Vince
KisMAC 0.3.3 in 32 bit mode + Aircrack-ng 1.1
ReplyDeletecan't install kismac please help
ReplyDeleteSure...
ReplyDeleteAre you trying to install kismac on a fridge?
no its a brand new HP pc with 7 home premium. .dmg is doing nothing?
ReplyDeleteihave tried 10 time fucking fedup
Ah, Windows 7, ok...
ReplyDeleteDo You have an error when you try to install? Something like Err Id 10 T
Probably the DMG on Win7. Try with KisMAC.exe
Hi, i tried, and i recover 140.000 uniques, but i try and fail, i forget "keep everything" now im trying again, i have a mac, SL, with only airport express so no reinjects avaliable. some tip?
ReplyDeleteHey there,
ReplyDeleteShould I stop scanning the available networks while running a weak scheduling attack (both), or just let it continue to run?
It's taking forever; OS Snow Leopard, Airport Extreme Passive mode, with over 2,000,000 packets collected. I've had weak scheduling going for over 24 hours and no luck. Would turning off the scan help at all or am I destined to wait forever?
Thanks in advance for any advice!
-J
-J
ReplyDeletenothing personal, but:
read step 4 again, and the first paragraph again.
"Before you post a question, PLEASE be sure to Read the 3 following post:
KisMAC + KisMAC troubleshooting + KisMAC Q & A
Once you are sure that the answer to your question can not be found, Please, Post your question in the Q&A Article: CLICK HERE.
ALL QUESTIONS WITHOUT KisMAC Version and OS Full Version will be ignored. Please Include Model and FCC number of the Network Adapter (the USB thingy) if applicable. And YES the FCC number is on it! and NO, it's not the MAC address.
"
mbp osx 10.7 2.3ghz quad core i7 kismac 0.3.3 alfa awus036h fcc id : UQ2AWUS036H
ReplyDeletei feel as though my mbp is not running wordlists (for wpa crack) as fast as it could be, according to activity monitor, I'm using 13-15%. and thats with safari and pages and several other things running too. also, kismac says its running 0.02/sec as far as words go, yet the counter is jumping in 500 word intervals every ~2 seconds. can i get it to go faster and how? would having more packets help? i have the hand shake. the last time i did a weak scheduling attack on a wep network i was using ~80 % cpu if memory serves.
thanks
Rh,
ReplyDeletefirst, Thanks for posting your specs.
"kismac says its running 0.02/sec as far as words go"
yup, it's a bug...
"I'm using 13-15%."
weird, I would try a "open in 32-bit" as stated in troubleshooting
"would having more packets help?"
Packets are worth NOTHING for WPA (as stated in troubleshooting....)
"can i get it to go faster and how?"
How fast do you want it to go? 10% or 5,000,000% faster?
Because I can run 100,000,000 passwords in 40 seconds, and it's explained in the blog....
Hello,
ReplyDeleteI'm trying to crack a WPA2 network with my built-in Airport Extreme Broadcom BCM43xx chipset in my MBP.
Is it possible to capture 4-way handshakes with this chipset using Kismac? Or do I need a card that supports injection?
Please help me!
Dear,
ReplyDeleteYour question has been answered multiple times.
Nothing personal, but your post will be removed for the sake of clarity. Nevertheless, Thanks for reminding me to do some dusting.
Hi,
ReplyDeleteI understand your frustration answering the same questions over and over. However, I have searched and searched for an answer that to this question and there is none.
Lot's of info about injection and deauthenticating, more about purchasing chipsets off amazon and ebay. Nothing about HOW TO capture a handshake without deauthentication.
What's passive mode then?
ReplyDeleteFrom what I can see passive mode is for collecting packets and unique IV's for WEP cracking. Can't see anything that says it collects handshakes for WPA encryption.
ReplyDeleteAre you suggesting that by scanning in passive mode, it will collect handshakes?
the process is the same: rfmon
ReplyDeletewithout a "Chipset" You'll just need the patience of Buddhist monk
Quoted
"How to crack WEP / WPA with Airport Extreme, Passive mode
WITHOUT Injection Device (Airport, Airport Extreme Alone)"
Ok, enough said. I've ordered an Alfa AWUS036H and in the meantime I will test my patience.
ReplyDeleteThank you!
Joking aside, your comments are showing that you do not grasp completely the concept behind the handshakes, what is a deauth or a flood.
ReplyDeleteCapturing it is the easy part. Then comes the Encryption ....
I would highly suggest that you read about the handshakes, deauth and flood before attempting to crack the encryption.
I will delete your posts and mine as they are redundant.
good luck
---- Step 5
ReplyDeleteIf the Column ENC is “NO”, the network is OPEN: No need of cracking anything ---
I attempted to join an open network by selecting "Join Network" under the Network tab. Why isn't this working ?
Also, all of the networks my airport picks up (without using Kismac) say a WPA password is required... the option of joining an open network from the airport alone is not an option.
ReplyDeleteHi all, I have two questions regarding the WEP cracking.
ReplyDeleteIt is taking a long time to collect IV's. If I quote this tutorial :
"500,000 packets for weak scheduling attack on a 40/64-bit WEP" Is this mean that I don't need a lot of IV's and I just stay focus on the number of normal packet ? 500K to 2000K ?
From my calculation, it will take 2 days to have 1000K packets and 20 to have the150K IV's that is why I wanted to know if with just the packets it will work
My other question is that the WEP network is changing the channel every 4 days (goes Channel 6 to Channel 11 and go back to Channel 6 ...) Do I have to start over each time the channel is changing ?
Thank you everyone and have a good day
"500,000 packets for weak scheduling attack"
ReplyDeleteWell, we have to change that. it's too confusing for people.
Only IV's are needed.
The number of Iv's you can collect depends on the traffic and if you are re-injecting or not.
2 days seems an awful lot to me.
A weak scheduling is basically a statistical attack. the more Iv's the greater the chance.
"Do I have to start over each time the channel is changing ?"
No.
Hi! I have EXACTELY the same issue of a guy here in the blog : "Im using KISMAC 0.3.3 and TL-WN321G on RT73 device. Everything looks correct, but I CAN´T reinject packets because appears NO SSID or HIDDEN SSID. " but you said that the question was already answered. Could you please tell me what were the question? Thank you for your time..
ReplyDeleteAre you on Windows?
ReplyDelete-2 questions left.
I'm on 10.7.2 Lion 64 bit. I have a WN321G v. 2 device. Do you need other additional information?
ReplyDeleteIt's in troubleshooting
ReplyDeletesorry man.....one question....i'm trying to crack MY wpa with an external usb wireless card that have the chip rtl8187L with my mac....i go to preferences-drivers...i added my usb wifi card and i check all the boxes that you explain in your video....then i go to the main page of kismac....i click on start scan but nothing appear! no one wifi lan! Where is the error? how can i solve this issue??? My card is not right to do this? have i to install particular drivers before start trying to crack???have to install some drivers???
ReplyDeletefucking love this blog!
ReplyDeletekeep up the good work, Admin!
I don't get it I have like 700,000 unique IVs gathered at once on a WEP signal, but when I do “Weak Scheduling Attack” >>> “Against Both” after less than a minute kismac tells me that cracking was unsuccessful.
ReplyDeleteI already had this message on other signal but it was with fewer IVs and after a long time of calculation. Can someone help?
ALL QUESTIONS WITHOUT KisMAC Version and OS Full Version will be ignored. Please Include Model and FCC number of the Network Adapter (the USB thingy) if applicable. And YES the FCC number is on it! and NO, it's not the MAC address.
ReplyDeleteOops sorry here are the missing info from my previous question:
ReplyDeleteOS: 10.7.4
FCC ID: UQ2AWUS036H
Kismac: 0.3.3
HK,
ReplyDeleteThere is always the possibility that your dump is corrupted.
Second, I am extremely sad to say so, but KisMAC is getting old.
I would encourage people to use KisMAC for the GUI, GPS, etc, but the crack itself should be conducted with Aircrack-ng (for WEP) see the post on this blog.
If you still can't figure it out, send me the dumpfile, I'll take a look at it. Dropbox is preferred.
Aircrack on os 10.6.8 is bunk. You'll get an error "wireless tools not found"
DeleteGood Job!
DeleteI particularly enjoy your undoubtful, questionless, unconcerned self-certainty.
Then it must absolutely be "bunk".
*Facepalms*
10-30 10-3
I have a rosewill n600ube can i inject with this? I dont have the mac disc either. How can i make aircrack work? Emaol me at jarelivory@gmail.com please.
ReplyDeleteSeriously?
DeleteHi,
ReplyDeletewhenever I get a sufficient amount of packets and IVs that would allow me to crack a WEP network, I click on Weak Scheduling Attack against both and nothing happens. Nothing loads, just nothing. It just keeps scanning as if I had not clicked on anything. What might be the problem?
OS: 10.9.2
KisMAC: 0.3.4
Mike,
Deletethat's a though one as I don't know what you have captured. Logic would be that even if the .kismac file was corrupted, you should load something.
I would take a wild guess and blame 10.9 with KisMAC altogether
Zip and Upload your file on Dropbox and send me the link . It will NOT be published. I'll take a look at it.
Any update on that issue?
DeleteI had got same problem.
Mac 10.10.2
Kismac 0.3.4
Same answer,
DeleteZip and Upload your file on Dropbox and send me the link . It will NOT be published. I'll take a look at it.
I'm now running KisMAC version 0.3.3, with OSX Mavericks 10.9.2. When I opened up KisMACS the second time (first time worked perfectly), nothing comes up when I hit the "Start Scan" button. I've already deleted "org.kismac-ng.kismac.plist" from my preferences folder, which the KisMAC FAQ stated was the problem. However, it's still not working. What did I do wrong?
ReplyDeleteuse kismac 0.3.4
DeleteThanks, that did help. However, now I'm having some more problems:
Delete1. I can't seem to get KisMAC to export its files with a .pcap extension, only with a .kismac extension. I've already checked the driver preferences for the "save everything" option.
2. Scanning constantly brings up repetitive copies of the same network. (eg. linksys appearing multiple times on the list) Is this normal?
1) Have you tried to simply rename the file and change the extension?
Delete1a) There is a search box on the top left. Try "PCAP". Then you can use command-F to find "PCAP" within the page(s).
2) is it the same same same network? i.e identical "SSID" and "BSSID". I see a lot of Toyota on the road, but they don't have all the same license plate. ;-)
1) Yes, renaming my saved .kismac file and using it in aircrack doesn't work, since it states that it is in an unsupported file format.
ReplyDelete1a) Do you mean the search box on the top left of KisMAC? If so, nothing shows up when I type PCAP. (Or when I search in Finder).
1b) When looking in my folders, I found that my dumplogs were somehow saved in my user folder. *facepalm* Do I change the save location in the preferences --> driver ---> "save dump at"? What's the difference between the contents of a .kismac and a dumplog file?
2) Same network name, different BSSID. My home network (whose name is unique) is repeated, along with some other neighboring networks (which show up in the regular wifi settings) and new ones that only appear in KisMAC. Also, extra copies of the network have far less packets than the first ones to show up.
Thanks for helping!
1) I am going to need proof of that, since that's what I have been doing that since 2007.
Delete1a) nope, I mean search the blog. My apologies for the lack of clarification.
1b) "*facepalm*" Welcome to the club. :) the ~ (tilde) indicates home folder, it's a convention. You better read about Unix and terminal, or you'll have some surprises. Have you tried to drag a file into the Terminal window? No? try it.
1b #2) close to none. the extension is different, that's pretty much it. you can open the file the file with Wireshark and dig into it.
1b #3) Search PCAP in blog.
2) mmmm... I would need a copy of that file. Are you on passive mode? Some routers have "protection" and will skip channels if they receive Dehauth frames or injection, and that could be a (far fetched) possibility. It could also be a bug.
Sorry for not replying sooner.
Delete1) Not sure how I should prove it, but here's the terminal output:
User1:~ user1$ aircrack-ng /Users/User1/Downloads/KisMAC/dumplog.pcap
Opening /Users/User1/Downloads/KisMAC/dumplog.pcap
Unsupported file format (not a pcap or IVs file).
Read 0 packets.
No networks found, exiting.
Quitting aircrack-ng...
Note: The dumplog.pcap was the file I renamed.
2) Here's a screenshot for KisMAC, if it helps:
http://tinypic.com/r/2qimcnm/8
Yes, I was on passive mode. I don't have an injection device, only Airport Extreme.
1) 88 KB
Delete2) It's weird. MidAutumn is supposed to have WPA2 encryption.
The .pcap is here: https://www.dropbox.com/s/rzeshg613e1sc68/dumplog.pcap
As per your DumpLog provided:
DeleteYou are not using a packet dump, but you are renaming a .kismac file. That's why it's going haywire.
just use the DumpLog file
Wifi Does not working when i tried to "Start Scan".
ReplyDeleteKindly do help me on that
Please, Kindly read the blog.
DeleteThat's the purpose of it: Not having to repeat every single time what to do.
when i start scanning again for the 2nd time, to see the list of wireless, nothing is happening
ReplyDeletei don't know whats wrong
i need some help please
Your solution is here
Deletehttp://easymactips.blogspot.com/2011/01/reminder.html
You're welcome!
Worked great for wep hack gonna try the wpa dictionary attack now
ReplyDeleteThe longest part is collecting the unique iv's
For test purposes, Kismac is fine with WPA, but it's really on the slow side.
DeleteCheck this blog for Aircrack, Pyrit and John The Ripper.
Pyrit on precomputed tables is, with no contest, the fastest. (by a humongous margin)