Photoshop Elements For Mac: How to install Actions
I know ... once you know how to do it, it's simple. It's just that I have to find a simple 101 way on how to do it. I admit it: Not that I am a dummy, but I just need a clear & simple explanation. Are you like me? Good ....
So, here we go, Step by Step....
Instructions for adding an Action to Photoshop Elements on a MAC
First you need to download an Action, you can find them free of charge. Just Google it and you'll find score of them or go at the end of this article for links ( If you ad the actions one by one, you'll have to repeat the following steps each time )
As a Ante Scriptum, not all of them will work; Depending on your OS and on your Photoshop Version. I have Photoshop Elements 6, the latest one is 8. If you feel sorry for me, you can send me the latest version; I'll gladly accept it.
Download the action(s) and put on it the desktop
An Action is composed to UP to 3 files:
.atn : The Action itself
.png : The Action "icon"
.xml : The Action "Instructions"
You may or may not have to have the 3 files, sometimes just one is provided.
With Finder click on the Hard drive icon ( Macintosh HD ) ( NOT the ~ User/ name / .... Folder)
Go to the Library Folder Then go to Application Support >> Adobe >> Photoshop Elements >> 6.0 >> Photo Creations >> Photo Effects
Drop the .atn and the .png files in this Folder Location.
Note: Not all actions will come with a .png, it's fine... you’ll just need to know that the action will display with a blank box, or you can create your own .png as example.
If you hover on the blank icon action, you'll see the name.
IF a .xml file was provided, repeat the steps (copy etc) and place the .xml file in the folder:
HD \ Library \Application Support \ Adobe\Photoshop Elements \ 6.0 \ Locale \ en-US or your own locale \ Photo Creations Metadata \ Photo Effects
Within Finder go to Library >> Application Support >> Adobe >> Photoshop Elements >> 6.0> Locale >> en_US. or your own locale Rename the “MediaDatabase.db3” file into “MediaDatabase_OLD.db3”
KEEP IT as copy or backup. If you are like me, you'll backup the backup.
Close Finder.... Now you can open Adobe PSE 6.0.... After few seconds, you should see a status box saying “Building content & effects”
After the update is complete you should find the actions on the Right side of the screen in the tool box/bar. Go to Effects > Photo Effects and display all
Notes:
! Don't use name longer than 30ch for Action file, it (seems that) it may interfere in some way
! If you plan on doing it more than once, just create a shortcut to the folders (Make Alias) It will make your life much easier: One Click and you can drop Actions in the right place.
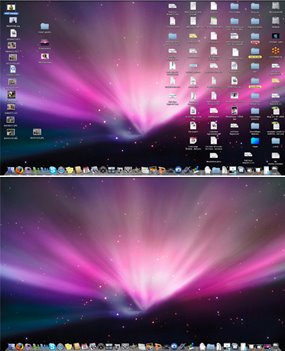
 If you downloaded an Action file AND a .png together, it's all good. If not, you will not see the action "icon" on the "Effects" table
If you downloaded an Action file AND a .png together, it's all good. If not, you will not see the action "icon" on the "Effects" tableExample:
Blue Arrow: Action with a .png associated (You have an icon)
Red Arrow: Action with NO .png associated (No Icon.. create one:-)
If you want to create your own .png , feel free. Just grab one from the folder and modify to make your own. Name the .png with the same root name as the action. i.e refine.atn & refine.png , and you'll be good to go. (don't forget to place it in the same folder too...) Or you can use a picture, use the action on it, and save it as a 64x64 png file.

Folders
Depending on where you'll drop your Action file, the Action will be located on a different Effects table in Photoshop. In this example, we tell you to drop in:
~Adobe >> Photoshop Elements >> 6.0 >> Photo Creations >> Photo Effects
But you may drop it in your folder of choice. i.e Filters , etc.
Download Actions
Links provided "AS IS" with no warranty whatsoever implied or not
Photoshop Elements 6 Actions Coffee & Tea Photography (Great set of Actions)
Vintage / Retro, Retouching etc
Panos Actions
Symmetry
Rainy Day
Border and Bend
Out of bounds
High Pass Sharpening
Old Goodies (Set)